 www.404media.co
www.404media.co
**Comment** I hope nobody loses their shirt over this. **Summary** * *Sensitive data exposed*: Internal code, infrastructure diagrams, passwords, and other technical information were publicly accessible on GitHub for months. * *Source unclear*: Unclear if an outside hacker or Binance employee accidentally uploaded the data. * *Potential risk*: Information could be used by attackers to compromise Binance systems, though Binance claims "negligible risk". * *Data details*: Included code related to passwords and multi-factor authentication, diagrams of internal infrastructure, and apparent production system passwords. * *Binance response*: Initially downplayed the leak, later acknowledged data was theirs but downplayed risk. * *Current status*: Data removed from GitHub via copyright takedown request. * Unclear if any malicious actors accessed the data.
 youtu.be
youtu.be
**Summary** Germany's renewable energy share reached a record 55% in 2023, driven by capacity expansion and favorable weather. This significant jump brings the country closer to its ambitious 2030 target of 80% green energy. Offshore wind led the way, followed by solar and biomass. The government's simplification of approval processes is credited with boosting growth. Power demand decreased due to economic slowdown and prioritizing renewables over fossil fuels. Despite temporary price spikes in 2022, day-ahead power prices stabilized in 2023, reflecting the increasing role of renewables. Overall, these developments highlight Germany's progress and the challenges it faces in its transition to a sustainable energy future.
 www.bleepingcomputer.com
www.bleepingcomputer.com
 **The issue:** Android users with Firefox can't access Google Search (including intl sites and localized domains like google.de, .co.uk, .com.br). Instead, they see a blank page. **Cause:** A server-side bug on Google's end related to User-Agent (UA) sniffing, which serves an empty page to newer Firefox versions. **Affected versions:** All Firefox versions on Android (>= 65) including Mobile 121.0, Nightly 123, and older. **Chrome not affected:** The bug is specific to Firefox. **Solutions:** * Use a different browser (Chrome, etc.) or search engine (DuckDuckGo). *Advanced users can:* * Change Firefox's UA in developer settings or with add-ons. * Request the desktop version of Google from Firefox settings (region-dependent). **Status:** * Problem identified as critical and escalated. * Still unresolved at the time of reporting. **Additional notes:** * Disabling Firefox's Enhanced Tracking Protection doesn't fix the issue. * Some users report google.co.in loading the desktop site instead of mobile.
 **Summary** * First cub sighting in 10 years: Camera captures a mother tiger with two cubs in Thailand, a major boost for the species. * Population boom: Tiger numbers skyrocket, from 46 in 2007 to potentially 190 now, making Thailand the only Southeast Asian country with significant growth. * Conservation works: Thailand's efforts, like anti-poaching measures and reduced human activity, are paying off. The country can now even become a source of tigers for struggling neighbours. * Hope for the future: With a thriving population and suitable habitat, tigers seem set to flourish in Thailand's western rainforests. **Comments** However good this is, I personally wouldn't want to run into one of these in the wild.
 www.bbc.com
www.bbc.com
 **Main findings:** * The seasons, especially winter, can affect our mood, memory, concentration, social behavior, and sex drive. * Shorter daylight hours are linked to winter blues and Seasonal Affective Disorder (SAD), characterized by low mood, sleep issues, and energy loss. * Reduced light disrupts our circadian rhythm, impacting mood and cognitive function. * Vitamin D deficiency (from less sunlight) might also contribute to winter blues and cognitive decline. * We may subconsciously seek warmth and social connection during colder months, explaining increased interest in romance films and social activities. * Sexual activity fluctuates across seasons, potentially due to the desire for physical and emotional warmth. **Key takeaways:** * Embrace positive aspects of winter like its beauty and coziness to improve mood. * Cognitive behavioural therapy can help managing negative thoughts and boost winter well-being. * Don't be hard on yourself if you're forgetful or less social during winter; it's natural. * Actively seek social connection and engage in activities you enjoy to combat winter blues. * 2019 Cochrane Systematic Review concluded that the evidence for light therapy's effectiveness as a preventative treatment was limited.
 Elephant0991
8 months ago
•
100%
Elephant0991
8 months ago
•
100%
Yeah, we need a branch of physics that turn existence into non-existence. Wait, weren't there some Infinity Stones?
 Elephant0991
8 months ago
•
100%
Elephant0991
8 months ago
•
100%
which shall be now known as the pawtop.
 Elephant0991
8 months ago
•
100%
Elephant0991
8 months ago
•
100%
Probably got some parachute built in.
 thehackernews.com
thehackernews.com
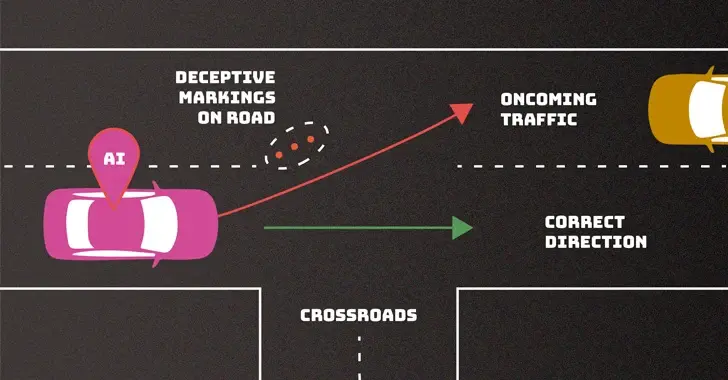
 **Key Points:** * Security and privacy concerns: Increased use of AI systems raises issues like data manipulation, model vulnerabilities, and information leaks. * Threats at various stages: Training data, software, and deployment are all vulnerable to attacks like poisoning, data breaches, and prompt injection. * Attacks with broad impact: Availability, integrity, and privacy can all be compromised by evasion, poisoning, privacy, and abuse attacks. * Attacker knowledge varies: Threats can be carried out by actors with full, partial, or minimal knowledge of the AI system. * Mitigation challenges: Robust defenses are currently lacking, and the tech community needs to prioritize their development. * Global concern: NIST's warning echoes recent international guidelines emphasizing secure AI development. **Overall:** NIST identifies serious security and privacy risks associated with the rapid deployment of AI systems, urging the tech industry to develop better defenses and implement secure development practices. **Comment:** From the look of things, it looks like it's going to get worse before it gets better.
 youtu.be
youtu.be
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Yeah, it's freakish because everything looks all wrong.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Of course if you care to look carefully, and sometimes closely.
 www.bbc.com
www.bbc.com
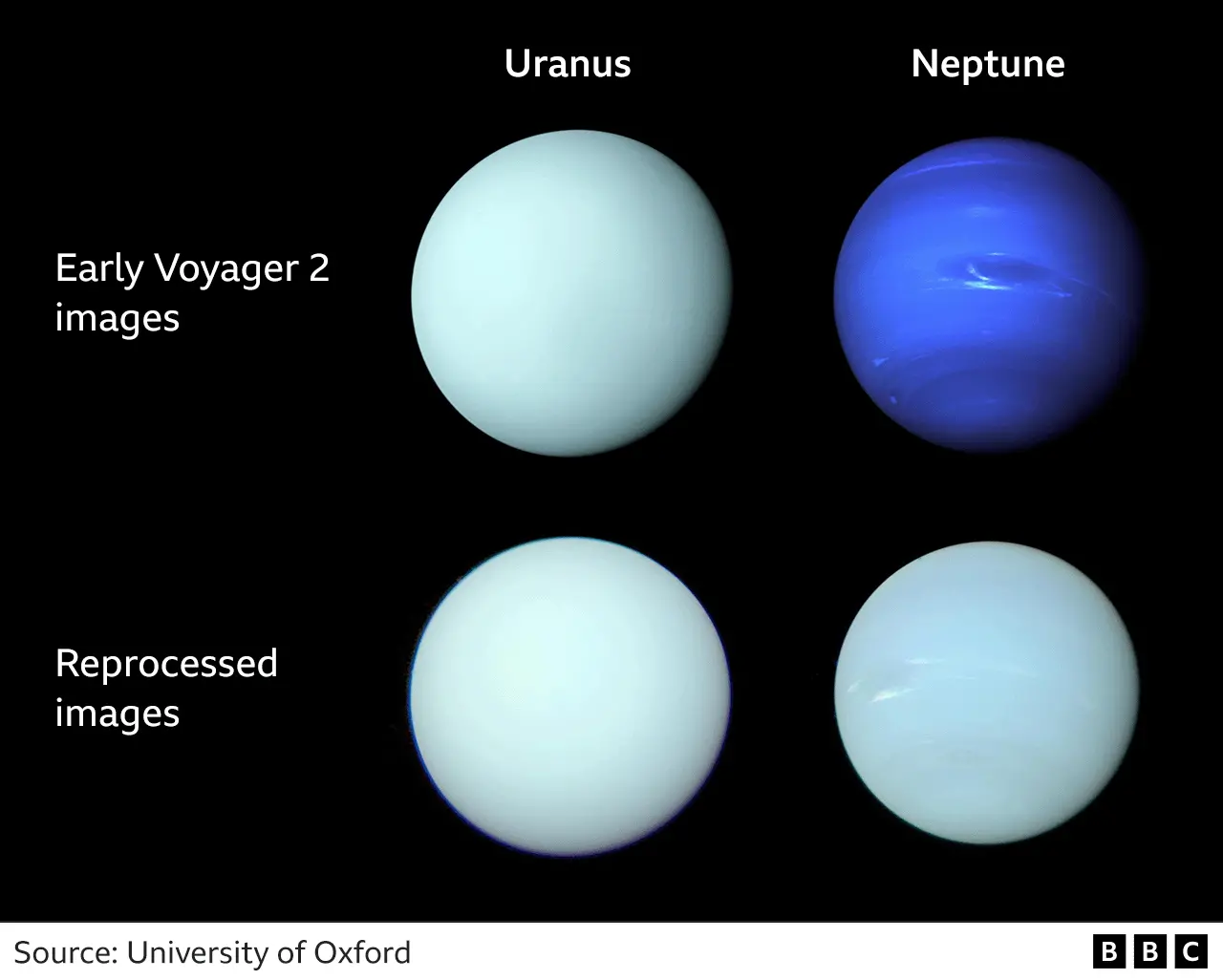 * Previous images of Neptune and Uranus, particularly from Voyager 2, were inaccurately blue and green due to image processing for detail enhancement. * New research analyzed data from Hubble and VLT telescopes to reveal their "true" colors are both a similar shade of greenish-blue. * Neptune still has a slightly bluer tinge due to a thinner haze layer. * Uranus may appear slightly greener in summer/winter but bluer in spring/autumn due to its unique tilt. * This research corrects a long-held misconception about these distant planets.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Smiling ain't gonna save ya!
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Deeply discounted, yet with the satisfying conclusion that our external clients get! /s
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
"Don't even think about petting me."
 time.com
time.com
**My favorite:** ***We found out that joy matters*** Joy is a vital human emotion—but as researchers noted in 2020, "surprisingly little" study has investigated exactly what it means and how to experience more of it. In 2023, that started to change. Researchers from more than a dozen institutions, including Harvard and the University of California, Berkeley, teamed up to determine whether performing micro-acts of joy changes how people feel in the short- and long-term, and whether there are differences based on factors like age, race, and location. Inaugural data from the BIG JOY Project—the world's largest citizen science project on joy, with nearly 70,000 participants spanning more than 200 countries—were released in November. Among the findings: Daily micro-acts of joy, like making a gratitude list or practicing positive reframing, helped participants experience a 25% increase in emotional well-being, 34% boost in levels of coping perception, and 12% jump in self-reported sleep quality over the course of a week. People can still sign up to participate in the project, and published research further quantifying the benefits of joy is expected in 2024.—Angela Haupt **Summary** ***Health and Science:*** * COVID-19 deaths fell significantly: Thanks to widespread vaccinations and treatments, COVID-19 deaths plummeted compared to previous years. * Life expectancy rose: With fewer fatalities from the virus, life expectancy in the U.S. started to climb back up. * Major advances in surgical science: Doctors achieved remarkable feats like transplanting animal organs into humans and performing the world's first whole-eye transplant. * CRISPR gene-editing for a disease: Patients with sickle cell anemia received the first-ever CRISPR treatment for a disease in the U.S. ***Climate and Environment:*** * Electric vehicles reduced fossil fuel demand: EVs made a noticeable dent in global oil use, paving the way for a cleaner future. * Good climate ideas became action: Innovative clean energy solutions like long-lasting iron-air batteries and carbon-based thermal batteries moved from concept to reality. * A landmark treaty for the High Seas: A new agreement established a legal framework for protecting previously unregulated ocean areas. * COP28 acknowledged the problem and solutions: Climate negotiations finally recognized the need to transition away from fossil fuels and ramp up renewables. * Climate lawsuits started making a difference: A growing number of legal cases pushed governments and corporations toward responsible environmental practices. ***Other Improvements:*** * Violent crime declined: Across the U.S., violent crime rates dropped significantly. * More scientific studies became free: Open access initiatives made research data more accessible to the public. * Joy was scientifically proven to matter: A large-scale project demonstrated the positive impact of daily micro-acts of joy on well-being and sleep. Overall, 2023 was a year marked by progress in various areas despite ongoing challenges. From advancements in healthcare and climate action to a renewed focus on mental well-being, these positive developments offer hope for the future.
 www.goodnewsnetwork.org
www.goodnewsnetwork.org
 **Key points:** * First-time painted dog mother abandons 8 pups at Potawatomi Zoo. * Golden retriever named Kassy becomes surrogate mother to pups. * 3 pups survive despite initial struggles due to missing pack interactions. * Pups, named Blue, Red, and Orange, won't immediately rejoin painted dog pack to avoid conflict. * Story highlights animal care difficulties, endangered species survival, and zoo conservation efforts. **Additional details:** * Painted dogs endangered due to habitat loss and hunting. * https://en.wikipedia.org/wiki/African_wild_dog
 techcrunch.com
techcrunch.com
cross-posted from: https://zerobytes.monster/post/5063838 I guess if the law firm handles its own data breach this way; you can expect the companies to handle the breaches the same way. **Summary** The international law firm Orrick, Herrington & Sutcliffe, specializing in handling security incidents for companies, suffered a cyberattack in March 2023, resulting in the exposure of sensitive health information belonging to over 637,000 data breach victims. The stolen data included consumer names, dates of birth, postal address and email addresses, and government-issued identification numbers, such as Social Security numbers, passport and driver license numbers, and tax identification numbers. The data also includes medical treatment and diagnosis information, insurance claims information — such as the date and costs of services — and healthcare insurance numbers and provider details. Orrick, serving as legal counsel during security incidents at other companies, revealed that the breach also affected clients such as EyeMed Vision Care, Delta Dental, MultiPlan, Beacon Health Options, and the U.S. Small Business Administration. The number of affected individuals tripled since the initial disclosure. Orrick reached a settlement for class action lawsuits in December, which accused Orrick of failing to inform victims of the breach until months after the incident, acknowledging the incident's impact and expressing regret for the inconvenience caused. The firm did not disclose details about the hackers' entry or whether a financial ransom was demanded.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Welcome to the 105: AI keyboard!
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
And definitely not standing at the back end!
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
A paramour came to a shitty end...
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
There began a night, wet and dreary...
Cool computers!
 web.archive.org
web.archive.org
**Summary:** The article discusses the phenomenon of microchimerism, where cells from a developing fetus can integrate into the mother's body and persist for years, potentially influencing various aspects of health. This bidirectional transfer of cells between mother and fetus during pregnancy is suggested to occur in various organs, such as the heart, lungs, breast, colon, kidney, liver, and brain. These cells, referred to as microchimeric cells, are genetically distinct entities that may play a role in immune system development, organ acceptance in transplantation, and even influencing behavior. Researchers propose that microchimeric cells might impact susceptibility to diseases, pregnancy success, and overall health. Studies in mice suggest that these cells acquired during gestation could fine-tune the immune system and contribute to successful pregnancies. The article explores potential benefits and drawbacks of microchimerism, including its role in autoimmune diseases, organ acceptance in transplantation, and pregnancy complications. Despite the widespread presence of microchimeric cells in individuals, many aspects of their function remain unclear, leading to debates among researchers. Some scientists believe that these cells may be influential architects of human life, potentially holding therapeutic implications for conditions like autoimmune diseases and high-risk pregnancies. However, challenges in studying microchimerism, including their rarity and hidden locations within the body, contribute to the ongoing controversy and uncertainty surrounding their significance.
 www.computerworld.com
www.computerworld.com
**Summary:** The author reflects on the challenges of memory and highlights a forgotten but valuable feature of Google Assistant on Android. The feature, called "Open memory," serves as a hub for Assistant's cross-platform information-storing system. Users can ask Google Assistant to remember specific information, and the "Open memory" command allows them to access a comprehensive list of everything stored, making it a useful tool for recalling details from any device connected to Google Assistant. The article emphasizes the potential of this feature for aiding memory and suggests incorporating it into daily habits for better recall.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Yes! There is this Buddhist saying, supposedly some 2,500 years back, "Even if a whole mountain were made of gold, not double that would be enough to satisfy one person."
You can trace unsatisfied greed in American gazillionaires all the way back to Rockefeller. Before that, you can trace it to Kings, Queens, Emperors, Conquerors. Only external circumstances, societal structures/cultures/etc, keep the greed in check. As soon as we were out of subsistence living, we started collecting, often times just for the sake of collections, sometimes other people's great misery be damned.
 Elephant0991
9 months ago
•
94%
Elephant0991
9 months ago
•
94%

 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
You figure out where you want to go. Plan how to get there, and then do things in the present to get there. Don't get stressed out how things turn out; you can only really have some notion of control of what you are doing. If the current plan doesn't work, change it, and keep doing it, until you get there, or not.

From: https://petapixel.com/2023/05/30/15-incredible-photos-from-2023-milky-way-photographer-of-the-year/
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
2FAS, Bitwarden, Firefox are my most used FOSS on Android for me.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
That seems totally workable. Spin it, and you have artificial gravity. You can be in fact riding a Spinning Space Dick.
 youtu.be
youtu.be
**Full Story** https://www.goodnewsnetwork.org/christine-crosss-dream-of-petting-a-penguin-is-fulfilled-for-christmas/ **Summary** An elderly woman named Christine Cross has always been a huge fan of penguins. For Christmas, her daughter Lindsay fulfilled Christine's lifelong dream of petting a real penguin at SeaWorld San Diego. Christine was so overcome with emotion that she cried tears of joy. Christine has always felt a connection to penguins because they are clumsy on land but graceful in the water, just like her. She collects anything penguin-themed and has sponsored penguins in zoos for years. Lindsay said that when she told Christine about the present, "she didn't say any words. It was more like an excited noise." After the experience, Christine couldn't stop saying thank you.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Cute dogs allowed!
 Elephant0991
9 months ago
•
95%
Elephant0991
9 months ago
•
95%
That's like, yenocide.
 Elephant0991
9 months ago
•
83%
Elephant0991
9 months ago
•
83%
Holy cow!
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Oh, the horror! I think I did the best I possibly could, given the circumstances.
 Elephant0991
9 months ago
•
91%
Elephant0991
9 months ago
•
91%
Welcome, to the Twilight Zone...
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Screwed!
But this is not a very good/logical/reasonable alien to be in contact with. There are so many ...ists with can call this alien. Generalization with sample of one? Pfff... They won't even get here...
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
It keeps getting bigger and better...
Pilipinas? This is definitely pornographic.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
I guess people will cheat and hide it everywhere.
 Elephant0991
9 months ago
•
90%
Elephant0991
9 months ago
•
90%
Lemmy!

These two news articles being consecutive is hilarious.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
There seem to be published scientific paper that some scientists disagreed. There are alcohol-free mouthwashes too.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
He's obviously using the Force.
 Elephant0991
9 months ago
•
100%
Elephant0991
9 months ago
•
100%
Listerine seems to help remove plaque effectively. Since start using it in the middle of the night when I wake up, not getting regularly cleaned doesn't seem to be a problem anymore. This is coupled with flossing and thorough brushing of course.
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
I hope to much thrilling from your audience. 👍 👍 👍
 Elephant0991
1 year ago
•
96%
Elephant0991
1 year ago
•
96%
While corporate America focuses on mainly profits, "fighting for human rights" are just empty slogan, because corporate America is already exploiting human misery for profits. For government, it's going to be "to prevent China from becoming the dominant tech power in the developing world" that's going to drive this sort of initiative, which most likely will have mixed results or fail miserably altogether. Chinese exports are already driving the non-elite consumer markets in the developing worlds.
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
Oh, come on, practically all the males have sex with their sometime lonely selves, and cameras are everywhere now. I'd personally put a privacy shutter on my webcam.
 www.bleepingcomputer.com
www.bleepingcomputer.com
**Summary** A new sextortion scam is circulating, impersonating YouPorn. Victims receive an email claiming that a sexually explicit video of them has been uploaded to the site and must pay to have it removed. In the past, similar scams threatened to share explicit content with contacts unless a ransom was paid, generating substantial profits. This recent scam claims to be from YouPorn, offering a free removal link that leads to nothing and lists paid options ranging from $199 to $1,399. Victims are urged to pay via Bitcoin. Thankfully, this campaign has not been successful, but it's important to remember that these emails are scams. If you receive such an email, delete it; there is no actual video, and making payments is not advisable.
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
That's a wonderful story. Thank you for sharing.
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
You definitely don't want this stuff to escape into the atmosphere.
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
Matching atmosphere. Like the floating door; you can be pushed right from inside the house onto the lawn.
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
Practically true.
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
That's like, real estate inspection.
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
When I forgot part of my my old password, I came up with a list of words that I possibly could have come up with and tried those. I eventually found it even if I was panicky the whole time. If I were you, I would list the words and try them in the order of probabilities.
Un/Fortunately, BW is implemented to rate-limit password brute-forcing. I feel you about your CAPTCHA hell, and I hate their surreal sunflower CAPTCHA (maybe to make it as repulsive as possible to the hackers?).
 www.freep.com
www.freep.com
 **Summary** Scout, a stray dog with a mysterious past and signs of abuse, escaped from an animal shelter and repeatedly found his way into a nursing home called Meadow Brook Medical Care Facility. After several visits, the nursing home staff adopted him as their own pet, bringing joy to the residents. Despite his troubled history, Scout displayed a strong bond with the elderly residents, comforting and protecting them. He became an integral part of their extended family, offering companionship and a sense of security.

by [long10000](https://web.archive.org/web/20161012220552/http://www.panoramio.com/user/2180746?with_photo_id=13659956) **Other views:**  by long10000  by [杨志强Zhiqiang ](https://web.archive.org/web/20161026170547/http://www.panoramio.com/user/4787542?with_photo_id=80797008)  by long10000  by long10000  by [David290](https://commons.wikimedia.org/wiki/User:David290)  by long10000
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
Didn't his admin approve the Operation Warp Speed thingy?
 Elephant0991
1 year ago
•
100%
Elephant0991
1 year ago
•
100%
That's probably not just for debris protection; there's also bat shit!
 gizmodo.com
gizmodo.com
**Short Summary** The macOS app called NightOwl, originally designed to provide a night mode feature for Macs, has turned into a malicious tool that collects users' data and operates as part of a botnet. Originally well-regarded for its utility, NightOwl was bought by another company, and a recent update introduced hidden functionalities that redirected users' data through a network of affected computers. Web developer Taylor Robinson discovered that the app was running a local HTTP proxy without users' knowledge or consent, collecting users' IP addresses and sending the data to third parties. The app's certificate has been revoked, and it is no longer accessible. The incident highlights the risks associated with third-party apps that may have malicious intentions after updates or ownership changes. **Longer Summary** The NightOwl app was developed by Keeping Tempo, an LLC that went inactive earlier this year. The app was recently found to have been turned into a botnet by the new owners, TPE-FYI, LLC. The original developer, Michael Kramser, claims that he was unaware of the changes to the app and that he sold the company last year due to time constraints. Gizmodo was unable to reach TPE-FYI, LLC for comment. However, the internet sleuth who discovered the botnet, Will Robinson, said that it is not uncommon for shady companies to buy apps and then monetize them by integrating third-party SDKs that harvest user data. Robinson also said that it is understandable why developers might sell their apps, even if it means sacrificing their morals. App development is both hard and expensive, and for individual creators, it can be tempting to take the money and run. This is not the first time that a popular app has been turned into a botnet. In 2013, the Brightest Flashlight app was sued by the Federal Trade Commission after allegedly transmitting users' location data and device info to third parties. The developer eventually settled with the FTC for an undisclosed amount. In 2017, software developers discovered that the Stylish browser extension started recording all of its users' website visits after the app was bought by SimilarWeb. Another extension, The Great Suspender, was flagged as malware after it was sold to an unknown group back in 2020. All of these apps had millions of users before anyone recognized the signs of intrusion. In these cases, the new app owners' shady efforts were all to support a more-intrusive version of harvesting data, which can be sold to third parties for an effort-free, morals-free payday. **Possible Takeaways** * Minimize the software you use * Keep track of ownership changes * Use software from only the most reputable sources * Regularly review installed apps * Be suspicious about app's unexpected behaviors and permissions
 freedom.press
freedom.press
**Summary** * The Marion County Record newsroom in Kansas was raided by police, who seized two cellphones, four computers, a backup hard drive, and reporting materials. * A computer seized was most likely unencrypted. Law enforcement officials hope that devices seized during a raid are unencrypted, as this makes them easier to examine. * Modern iPhones and Android phones are encrypted by default, but older devices may not be. * Desktop computers typically do not have encryption enabled by default, so it is important to turn this on manually. * Use strong random passwords and keep them in a password manager. * During the raid, police seized a single backup hard drive. It is important to have multiple backups of your data in case one is lost or stolen. * You can encrypt USB storage devices using BitLocker To Go on Windows, or Disk Utility on macOS. * All major desktop operating systems support Veracrypt, which can be used to encrypt entire drives. **Main Take-aways** * Encrypt your devices, drives, and USBs. * Use strong random passwords and password manager. * Have multiple backups.
 www.theregister.com
www.theregister.com
**Paper & Examples** "Universal and Transferable Adversarial Attacks on Aligned Language Models." (https://llm-attacks.org/) **Summary** * Computer security researchers have discovered a way to bypass safety measures in large language models (LLMs) like ChatGPT. * Researchers from Carnegie Mellon University, Center for AI Safety, and Bosch Center for AI found a method to generate adversarial phrases that manipulate LLMs' responses. * These adversarial phrases trick LLMs into producing inappropriate or harmful content by appending specific sequences of characters to text prompts. * Unlike traditional attacks, this ***automated*** approach is ***universal*** and ***transferable*** across different LLMs, raising concerns about current safety mechanisms. * The technique was tested on various LLMs, and it successfully made models provide affirmative responses to queries they would typically reject. * Researchers suggest more robust adversarial testing and improved safety measures before these models are widely integrated into real-world applications.
News article: https://techcrunch.com/2023/08/10/belarus-hackers-target-foreign-diplomats/ **News Summary** * A hacking group with apparent links to the Belarusian government has been targeting foreign diplomats in the country for nearly 10 years. * The group, which ESET has dubbed MoustachedBouncer, has likely been hacking or at least targeting diplomats by intercepting their connections at the internet service provider (ISP) level, suggesting close collaboration with Belarus' government. * Since 2014, MoustachedBouncer has targeted at least four foreign embassies in Belarus: two European nations, one from South Asia, and another from Africa. * ESET first detected MoustachedBouncer in February 2022, days after Russia invaded Ukraine, with a cyberattack against specific diplomats in the embassy of a European country "somehow involved in the war." * The hacking group is able to trick the target's Windows operating system into believing it's connected to a network with a captive portal. The target is then redirected to a fake and malicious site masquerading as Windows Update, which warns the target that there are "critical system security updates that must be installed." * It's not clear how MoustachedBouncer can intercept and modify traffic, but ESET researchers believe it's because Belarusian ISPs are collaborating with the attacks, allowing the hackers to use a lawful intercept system similar to the one Russia deploys, known as SORM. * Once ESET researchers found the attack last February and analyzed the malware used, they were able to discover other attacks - the oldest dating back to 2014 - although there is no trace of them between 2014 and 2018. * MoustachedBouncer’s activity spans from 2014 to 2022 and the TTPs of the group have evolved over time.
 www.malwarebytes.com
www.malwarebytes.com
**Summary** * Detroit woman wrongly arrested for carjacking and robbery due to facial recognition technology error. * Porsche Woodruff, 8 months pregnant, mistakenly identified as culprit based on outdated 2015 mug shot. * Surveillance footage did not match the identification, victim wrongly identified Woodruff from lineup based on the 2015 outdated photo. * Woodruff arrested, detained for 11 hours, charges later dismissed; she files lawsuit against Detroit. * Facial recognition technology's flaws in identifying women and people with dark skin highlighted. * Several US cities banned facial recognition; debate continues due to lobbying and crime concerns. * Law enforcement prioritized technology's output over visual evidence, raising questions about its integration. * ACLU Michigan involved; outcome of lawsuit uncertain, impact on law enforcement's tech use in question.
 addy.io
addy.io
**Summary** * AnonAddy has rebranded as addy.io. * addy.io is a privacy-focused email service that allows you to create and manage email aliases. Aliases are temporary email addresses that forward to your real email address. This can be useful for protecting your privacy when signing up for websites or services that you don't trust. * The name change was motivated by a desire for a shorter, easier to understand and more recognizable name. * The service will remain exactly the same, but with more features. * There is a also a new logo. * The web application is now a SPA (single page application). * The API has also been updated. * There are a number of new features. * For most users, there is nothing they need to do. * All existing alias domains are staying the same. The new addy.io domain will be available to those on paid plans shortly. * If you use a hardware key for 2FA on your account, you will receive an email notification shortly with further information. Edited based on comment from: @iso@lemy.lol
 gridinsoft.com
gridinsoft.com
**Summary** * Scammers exploit Twitter's rebranding (transition to name "X") confusion for phishing. * Twitter Blue users targeted, offered migration to "X," but scammers gain account access. * Phishing emails seem genuine, appearing to come from x.com and passing the Security Policy Framework (SPF), and include deceptive authorization link, opening a *legitimate API authorization screen*. * Clicking link grants attackers control over victim's Twitter account settings and content. * Victims can block access by revoking app authorization in Twitter settings. * Twitter is aware and "working on a solution." ::: spoiler Article's Safety Recommendations (probably a bit generic and self-promotional) 1) Being cautious with unfamiliar emails, especially attachments or links. 2) Verifying URLs by hovering over them. 3) Not sharing personal info on suspicious/unknown sites. 4) Be careful with attachments and links. 5) Using two-factor authentication (2FA) for account security. 6) Keeping antivirus software updated to prevent malware. ::: Edited based on comment from: @incogtino@lemmy.zip
**What are TunnelCrack vulnerabilities?** * Two widespread security vulnerabilities in VPNs can be abused by an adversary to leak traffic outside the VPN tunnel. * The two vulnerabilities are called the **LocalNet** and **ServerIP** attack. **Summary of what VPNs are vulnerable to TunnelCrack** * VPNs for ***iPhones, iPads, MacBooks, and macOS*** are extremely likely to be vulnerable * A majority of VPNs on ***Windows and Linux*** are vulnerable * ***Android*** is the most secure with roughly one-quarter of VPN apps being vulnerable. * Users generally decide which VPN protocol to adopt while creating the VPN tunnel, with common options being OpenVPN, WireGuard, or IPsec. As a result, the precise configuration of the client, and whether it is vulnerable to (variants of) our attacks, may depend on the chosen VPN server and protocol. **TunnelCrack Prevention** To prevent the attack, VPN clients should be updated to send all traffic through the VPN tunnel, except traffic generated by the VPN app itself. **How do the LocalNet and ServerIP attacks work?** ***LocalNet attack:*** * The adversary acts as a malicious Wi-Fi or Ethernet network and tricks the victim into connecting to it. * Once connected, the adversary assigns a public IP address and subnet to the victim. * The adversary then tells the victim that the local network is using this subnet, which means that IP addresses in this range are directly reachable in the local network. When the victim now visits a website with an IP address in this range, the web request will be sent outside the protected VPN tunnel. * 66+ VPNs on five platforms were tested and found that all VPN apps on ***iOS*** are vulnerable. Additionally, all but one VPN client on ***macOS*** is vulnerable, on ***Windows*** a large majority of VPNs are vulnerable, and on ***Linux*** more than one-third are vulnerable. Interestingly, VPN apps on ***Android*** are typically the most secure, with one-quarter being vulnerable to the LocalNet attack. ***ServerIP attack:*** * The adversary abuses the observation that many VPNs don't encrypt traffic towards the IP address of the VPN server. This is done to avoid re-encryption of packets. * The adversary first spoofs the DNS reply for the VPN server to return the IP address of a website that they control. The victim will then connect with the VPN server at this IP address. * To assure the victim still successfully creates a VPN connection, the adversary redirects this traffic to the real VPN server. * While establishing the VPN connection, the victim will add a routing rule so that all traffic to the VPN server, in this case the spoofed IP address, is sent outside the VPN tunnel. When the victim now visits a website with the IP address of the VPN server, the web request is sent outside the protected VPN tunnel. * Built-in VPN clients of ***Windows, macOS, and iOS*** are vulnerable. ***Android 12*** and higher is not affected. A significant number of ***Linux*** VPNs are also vulnerable.
 www.kasada.io
www.kasada.io
**Short summary:** This is a sophisticated malware campaign that is targeting inexperienced cyber criminals with the goal of stealing their cryptocurrency and other sensitive information. The campaign is using malicious OpenBullet configuration files to distribute the malware, and it is targeting criminal communities that are known to use cryptocurrencies. Other reading: https://thehackernews.com/2023/08/new-malware-campaign-targets.html
 www.malwarebytes.com
www.malwarebytes.com
**Summary** * AMP is an open-source HTML framework that makes web content load faster on mobile devices. * Researchers have found a new phishing tactic that uses Google AMP to make URLs look trustworthy. * The tactic involves using the URL of a web page cached by the Google AMP Viewer. This URL looks similar to the original URL, but it is actually served from the google.com domain. * This gives the malicious website the legitimacy of the google.com domain, which can trick users into entering their personal information. * The researchers found that the Google AMP URLs have proven to be very successful at reaching users, even in environments protected by secure email gateways. * Along with using Google AMP URLs, the researchers also saw other techniques being used in phishing attacks, such as open redirects on trusted domains, chains of redirects linking the AMP URL to the malicious site, image-based phishing emails, and CAPTCHA services to disrupt automated analysis. * To avoid phishing attacks, it is important to not take things at face value for messages requiring urgent attention. It is also important to use a phishing-resistant password manager and a FIDO2 2FA device.
Two pieces of string walk into a bar. The first piece of string asks for a drink. The bartender says, “Get lost. We don’t serve pieces of string.” The second string ties a knot in his middle and messes up his ends. Then he orders a drink. The bartender says, “Hey, you aren’t a piece of string, are you?” The piece of string says, “Not me! I’m a frayed knot.” from: https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
 www.eff.org
www.eff.org
**Summary** * Google's proposal, Web Environment Integrity (WEI), aims to send tamper-proof information about a user's operating system and software to websites. * The information sent would help reduce ad fraud and enhance security, but it also raises concerns about user autonomy and control over devices. * The authors argue that implementing WEI could lead to websites blocking access for users not on approved systems and browsers. * They express worries about companies gaining more control over users' devices and the potential for abuse. * The authors emphasize that users should have the final say over what information their devices share. * Remote attestation tools, like WEI, might have their place in specific contexts but should not be implemented on the open web due to potential negative consequences. * The authors advocate for preserving user autonomy and the openness of the web, emphasizing that users should be the ultimate decision-makers about their devices. Joke: > Two pieces of string walk into a bar. The first piece of string asks for a drink. The bartender says, “Get lost. We don’t serve pieces of string.” > The second string ties a knot in his middle and messes up his ends. Then he orders a drink. > The bartender says, “Hey, you aren’t a piece of string, are you?” The piece of string says, “Not me! I'm a frayed knot.”
**Summary:** * Generative AI will make it easier to produce disinformation that is tailored to specific audiences. * This means that disinformation campaigns will be more targeted and effective. * AI-powered disinformation could be used to target individuals with content that is specifically designed to manipulate them. * The Biden administration has taken some steps to address the threat of AI-powered disinformation, but it is unclear whether these steps will be enough. * It is important to be aware of the potential threats posed by AI-powered disinformation and to be critical of the content we see online. **Quotes:** > “If I want to launch a disinformation campaign, I can fail 99 percent of the time. You fail all the time, but it doesn’t matter. Every once in a while, the QAnon gets through. Most of your campaigns can fail, but the ones that don’t can wreak havoc.” > “This is the classic story of the last 20 years: Unleash technology, invade everybody’s privacy, wreak havoc, become trillion-dollar-valuation companies, and then say, ‘Well, yeah, some bad stuff happened.' We’re sort of repeating the same mistakes, but now it’s supercharged because we’re releasing this stuff on the back of mobile devices, social media, and a mess that already exists.”
 web.archive.org
web.archive.org
**Summary** * The article discusses the problem of non-consensual sharing of strangers' images and videos on social media platforms. * It highlights how people sometimes exploit strangers for viral content without considering the potential harm caused. * The author emphasizes the need for consent before posting someone's image or video and calls for a shift in societal norms regarding online privacy. * There is [a French law](https://www.buzzfeednews.com/article/stephaniemcneal/french-pass-law-protecting-kid-influencers) that entitles child influencers to demand that platforms scrub all trace of them once they turn 16. * The article suggests that platforms could implement tools to obtain consent from strangers before posting content featuring them. * Ultimately, the author argues that treating strangers with respect and obtaining their consent should become the standard in online interactions to foster a more ethical and civil internet culture.
 www.malwarebytes.com
www.malwarebytes.com
**Lay summary:** FakeSG is a new type of malware that tricks people into installing it by pretending to be a fake browser update. Once installed, FakeSG can give hackers remote control of your computer, which they can use to steal your personal information or install other malware. FakeSG is spread through compromised websites. When you visit a website that has been infected with FakeSG, you may be redirected to a fake browser update page. If you click on the update button, you will be tricked into installing FakeSG on your computer. **More technical summary:** * A new campaign called FakeSG has been discovered that uses compromised websites to trick users into running a fake browser update. * The fake updates look very professional and are more up to date than those used in the SocGholish campaign. * The threat actors are distributing NetSupport RAT either as a zipped download or via an Internet shortcut. * The installation flow for FakeSG is different from that of SocGholish, and it uses different layers of obfuscation and delivery techniques. * The NetSupport RAT files are hosted on the same compromised WordPress site used earlier to download the Internet shortcut. * Following a successful infection, callbacks are made to the RAT's command and control server. * Fake browser updates are a common decoy used by malware authors, and FakeSG is the latest contender in this space. **Other details:** * The FakeSG campaign uses different browser templates depending on which browser the victim is running. * The source code for the fake updates is loaded from one of several domains impersonating Google or Adobe. * The installation flow for FakeSG can also involve downloading a malicious URL shortcut. * The NetSupport RAT is a powerful remote access tool that can be used to gather information and perform additional actions on victims of interest.
 slashnext.com
slashnext.com
## Summary: * Generative AI is being used by cybercriminals to create more convincing and personalized phishing emails for Business Email Compromise (BEC) attacks. * This technology allows attackers to automate the creation of highly convincing fake emails, personalized to the recipient, thus increasing the chances of success for the attack. * One such tool is WormGPT, which is a blackhat alternative to GPT models, designed specifically for malicious activities. * WormGPT can create emails that are not only remarkably persuasive but also strategically cunning, showcasing its potential for sophisticated phishing and BEC attacks. The use of generative AI for BEC attacks has two main advantages: 1) **Exceptional grammar**: Generative AI can create emails with impeccable grammar, making them seem legitimate and reducing the likelihood of being flagged as suspicious. 2) **Lowered entry threshold**: The use of generative AI democratises the execution of sophisticated BEC attacks. Even attackers with limited skills can use this technology, making it an accessible tool for a broader spectrum of cybercriminals. To safeguard against AI-driven BEC attacks, organizations should implement the following measures: 1) **BEC-specific training**: Companies should develop extensive, regularly updated training programs aimed at countering BEC attacks, especially those enhanced by AI. 2) **Enhanced email verification measures**: Organizations should enforce stringent email verification processes.
 www.malwarebytes.com
www.malwarebytes.com
**Summary** - A zero-day vulnerability (CVE-2023-36884) is being exploited in the wild to target those with an interest in Ukraine. - The vulnerability allows attackers to execute malicious code on a victim's computer by tricking them into opening a specially crafted Microsoft Office document. - The attacks are being carried out by a group known as Storm-0978, which is also known for distributing trojanized versions of popular software and launching ransomware attacks. - Microsoft recommends that organizations use Microsoft Defender for Office 365 or the Block all Office applications from creating child processes attack surface reduction rule to protect themselves from this vulnerability. - Organizations can also consider blocking outbound SMB traffic. **Other details** - The phishing campaign that is being used to deliver the malicious Office documents is targeting defense and government entities in Europe and North America. - The bait used in the phishing emails is related to the Ukrainian World Congress, a non-profit organization of Ukrainian public organizations in diaspora. - Once a victim opens the malicious Office document, the attacker can execute arbitrary code on their computer. - The attacker can then use this code to steal data, install malware, or take control of the victim's computer. **Microsoft's CVE-2023-36884 specific recommendations** - Customers who use Microsoft Defender for Office 365 are protected from attachments that attempt to exploit CVE-2023-36884. - In current attack chains, the use of the Block all Office applications from creating child processes attack surface reduction rule prevents the vulnerability from being exploited - Organizations who cannot take advantage of these protections can set the FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key to avoid exploitation. Please note that while these registry settings would mitigate exploitation of this issue, it could affect regular functionality for certain use cases related to these applications. **Other recommendation:** - You could also consider blocking outbound SMB traffic.