Sidebar
Netsec
 therecord.media
therecord.media
A 22-year-old Frenchman [was sentenced](https://www.justice.gov/usao-wdwa/pr/member-notorious-international-hacking-crew-sentenced-prison) on Tuesday to three years in U.S. federal prison for his participation in the ShinyHunters hacking group. Sebastien Raoult, also known as “Sezyo Kaizen,” was extradited to the U.S. in January 2023 after his arrest in Morocco the year before. He pleaded guilty to conspiracy to commit wire fraud and aggravated identity theft and is also required to pay $5 million in restitution. According to an indictment from prosecutors in the Western District of Washington, Raoult and two co-conspirators hacked more than 60 companies around the world and posted stolen data on dark web forums like RaidForums, EmpireMarket and Exploit. In some cases, they threatened to leak data if a ransom was not paid. In 2020 and 2021, ShinyHunters [perpetrated](https://intel471.com/blog/shinyhunters-data-breach-mitre-attack) a series of hacks on well-known entities, including breaches of the clothing retailer Bonobos, the photo app Pixlr and Microsoft’s GitHub account. It also [claimed](https://www.bleepingcomputer.com/news/security/atandt-denies-data-breach-after-hacker-auctions-70-million-user-database/#google_vignette) to have information from 70 million AT&T accounts, although the company denied it had been breached. According to the DOJ, Raoult and accomplices created spoof websites pretending to be the login pages of legitimate businesses, and sent phishing emails to company employees. When the victims entered their credentials, the hackers were able to gain access to their accounts. They stole “hundreds of millions of customer records” and inflicted an estimated $6 million in losses. “This is an extraordinarily serious offense. We’re talking about him robbing people of millions of dollars,” said U.S. District Judge Robert S. Lasnik at the sentencing hearing, according to a Department of Justice release. Raoult’s father [told](https://www.databreaches.net/sebastien-raoult-sentenced-in-federal-court-could-be-out-in-less-than-11-months/) DataBreaches.net that the sentence includes served time in Morocco and Seattle, meaning that he only has another 11 months to serve in prison. According to the DOJ, Raoult told the court: “I understand my mistakes and I want to put that part behind me. No more hacking. I don’t want to disappoint my family again.”
 www.theregister.com
www.theregister.com
Security experts claim ransomware criminals have got their hands on a functional exploit for a nearly year-old critical Microsoft SharePoint vulnerability that was this week added to the US's must-patch list. Without specifically identifying the gang, researcher Kevin Beaumont [said](https://cyberplace.social/@GossiTheDog/111738179459714278) that at least one ransomware group has a working exploit for the critical vulnerability, which can potentially achieve remote code execution (RCE) although the US Cybersecurity and Infrastructure Security Agency (CISA) said its use in ransomware campaigns is currently "unknown." When vulnerabilities are added to CISA's known exploited vulnerabilities (KEV) list, it means two things: Federal civilian executive branch (FCEB) agencies have three weeks to patch them, and they're being actively exploited by cybercrims. Tracked as CVE-2023-29357, the SharePoint vulnerability in question was first identified by Nguyễn Tiến Giang (Jang) of Singaporean security house STAR Labs. Back in March 2023, during Vancouver's Pwn2Own contest, he chained it with another bug to achieve unauthenticated RCE on a SharePoint server. CVE-2023-29357 is a critical elevation of privileges (EoP) vulnerability that carries a 9.8 severity score. Microsoft originally addressed this in [June 2023's Patch Tuesday](https://www.theregister.com/2023/06/13/june_patch_tuesday_vmware_vuln/), and Jang [published](https://starlabs.sg/blog/2023/09-sharepoint-pre-auth-rce-chain/) a detailed rundown of how the exploit chain was developed a few months later in September. Proof of concept (PoC) code for CVE-2023-29357 was [published](https://github.com/Chocapikk/CVE-2023-29357) to GitHub the following day, but wasn't constructed in a way that revealed how to chain it with CVE-2023-24955, or any other RCE bug, to achieve the pre-auth RCE exploit that earned Jang his $100,000 prize at [Pwn2Own](https://www.theregister.com/2023/03/27/in_brief_security/). Researchers warned in September that the publication of the PoC code provided a foundation from which cybercriminals could build a working exploit, and it was highly important to patch both vulnerabilities as soon as possible. Beaumont said at the time he expected ransomware attacks using the two vulnerabilities to begin "in [the] coming weeks." The addition to CISA's [KEV catalog](https://www.cisa.gov/known-exploited-vulnerabilities-catalog) means it has taken cybercriminals months to start exploiting the vulnerability, despite having the bare-bones tools to do so. When PoC code is published for any given vulnerability, attacks typically soar in the days after as baddies race to develop working exploits before organizations can plug the holes. The delay, in this case, might be explained by the difficulty involved in chaining CVE-2023-29357 together with CVE-2023-24955 – a feat Jang said took him and his team "nearly a year of meticulous effort and research" to achieve before demonstrating it at Pwn2Own. Microsoft addressed CVE-2023-29357 in June and CVE-2023-24955 in May 2023, but IT admins have been reminded that simply applying the June 2023 Patch Tuesday updates won't automatically protect their organizations. Manual, SharePoint-specific patches are required to ensure the fixes are applied properly as patches won't be installed by Windows Update. The EOP vulnerability itself was originally designated by Microsoft as "exploitation more likely" with a "low" attack complexity. "An attacker who successfully exploited this vulnerability could gain administrator privileges," its [advisory](https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2023-29357) reads. It also hasn't been updated since June to reflect the active exploitation. "An attacker who has gained access to spoofed JWT authentication tokens can use them to execute a network attack which bypasses authentication and allows them to gain access to the privileges of an authenticated user. The attacker needs no privileges nor does the user need to perform any action." CVE-2023-24955 was also designated "exploitation more likely" status with a "low" attack complexity, but carried a less severe rating of 7.2 due to privileges being required to remotely exploit it. According to an [advisory](https://digital.nhs.uk/cyber-alerts/2023/cc-4388) from NHS Digital, there is currently no known PoC code for the RCE vulnerability circulating online so those exploiting it will have developed it themselves and kept it a secret, for now.
 citizenlab.ca
citizenlab.ca
In a new study, Citizen Lab sheds light on the massive security threats facing Latin Americans. Citizen Lab and Open Technology Fund (OTF) fellow Beau Kujath in collaboration with SocialTIC finds that mobile applications in Latin America puts millions of users at a security and privacy risk. Beau’s research focuses on three types of mobile applications: telecommunication apps, government-developed apps, and marketplace apps. Millions of people in Latin America rely on these categories of applications for essential daily functions including cellular service, emergency response, healthcare, money transfers, and more. Thus, people are incentivized to keep these apps on their devices, leaving them vulnerable. ### Key Findings - A cellular management app from Mexican telecommunications giant MiTelcel consistently fetches images and JSON files for the splash configuration over cleartext HTTP. This vulnerability allows attackers to eavesdrop on the cleartext traffic and potentially inject their own malicious images that will be displayed on the app’s “Home” page. - The MiTelcel app sends POST requests to five different third party servers with personal info of the user including their email and phone number, although the app store’s description stated no personal info was shared with any third-parties at the time of analysis. - Another cellular management app from Mexican telecom SAT Movil uses cleartext HTTP for the “Chat” page that is responsible for communicating highly sensitive personal info including citizen ID numbers and passwords, allowing eavesdroppers to read these as they are transmitted over the network - A Salvadoran cryptocurrency app ChivoWallet checks with Microsoft CodePush servers each time it is opened to see if there is a new update available to fetch, granting the developers the ability to update its functionality on demand outside the trusted app store update mechanisms. - Three of the four telecommunication apps analyzed send SMS messages that include external links that are vulnerable to SSL strip attacks. These attacks allow an attacker to downgrade connections from HTTPS to cleartext HTTP in order to eavesdrop on the info exchanged and potentially inject their own malicious responses. The full detailed technical report includes more information on what live security and privacy issues found in the set of apps, how they were found and the motivation for this project. Github repo: [https://github.com/beaukuj15/relab](https://github.com/beaukuj15/relab) Read the full report [here](https://www.opentech.fund/wp-content/uploads/2024/01/ICFP_Beau_Kujath_Final_Report.pdf) (PDF). [Post by the OTF](https://www.opentech.fund/news/an-analysis-of-essential-latin-american-mobile-apps/)
 www.theregister.com
www.theregister.com
Two zero-day bugs in Ivanti products were likely under attack by cyberspies as early as December, according to Mandiant's threat intel team. The software biz disclosed the vulnerabilities in Ivanti Connect Secure (ICS) – the VPN server appliance previously known as Pulse Connect Secure – and its Policy Secure gateways on Wednesday. At the time the biz said someone or some group had already [found and exploited](https://www.theregister.com/2024/01/11/china_backed_ivanti_exploits/) the holes. A spokesperson for Ivanti told The Register the victim count was "less than 10." It has since increased. This situation is especially worrisome because neither flaw has a patch — Ivanti hopes to start rolling those out the week of January 22 in a staggered fashion, and, in the meantime urges customers to "immediately" deploy [mitigations](https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US). And as Mandiant Consulting CTO Charles Carmakal [noted](https://www.linkedin.com/posts/charlescarmakal_this-page-uses-javascript-please-enable-activity-7151062696304529410-KPQ1/): "These CVEs chained together lead to unauthenticated remote code execution." That means these flaws can be exploited to seize control of an organization's Ivanti network appliances and use them to drill into that org's IT environment. The two zero-days are: CVE-2023-46805, an authentication bypass bug; and CVE-2024-21887, a command injection vulnerability. However, as Carmakal told The Register, this number will likely increase. "We are learning about new victims as they run Ivanti's integrity checking tool and are seeing indicators of compromise," Carmakal said. "The list will likely continue to grow, as more organizations run the tool and discover their devices are compromised." Mandiant is working with Ivanti to help clean up the mess, and on Friday weighed in with its own [initial analysis](https://www.mandiant.com/resources/blog/suspected-apt-targets-ivanti-zero-day), promising to add more details as its investigation into the matter continues. A couple pieces of the analysis in particular stand out. First, Mandiant says it has identified in-the-wild abuse of the bugs as early as December by a previously unknown suspected espionage team it now tracks as UNC5221. Earlier probing by Volexity, which discovered the zero-day holes and privately reported them to Ivanti, linked the attackers to China. "Volexity has reason to believe that UTA0178 is a Chinese nation-state-level threat actor," it [said](https://www.volexity.com/blog/2024/01/10/active-exploitation-of-two-zero-day-vulnerabilities-in-ivanti-connect-secure-vpn/) Wednesday. When asked about a possible China link, Carmakal said there isn't enough data for attribution. In looking into the attacks, Mandiant saw that UNC5221 primarily used hijacked end-of-life Cyberoam VPN appliances as command-and-control servers in its attacks on Ivanti customers. "These compromised devices were domestic to the victims, which likely helped the threat actor to better evade detection," the threat hunters wrote. Additionally, the intruders used various pieces of bespoke malware to achieve persistence and avoid detection, allowing continued access to victims' networks. "This indicates that these are not opportunistic attacks, and UNC5221 intended to maintain its presence on a subset of high priority targets that it compromised after a patch was inevitably released," Mandiant noted. So far, the threat hunters have identified five custom malware families used by UNC5221 after it infiltrates a target via the Ivanti flaws. One is Zipline, a backdoor that receives commands to execute on compromised devices. It also supports file transfers in and out of infected equipment, can provide a proxy server, and can implement a tunneling server. Thinspool is designed to add malicious webshell code to legitimate files. This helps the cyber-spies establish persistence on compromised networks. It acts as the initial dropper for the Lightwire webshell. Yet another webshell, Wirefire, is stashed within Connect Secure appliances for remote control of the devices. It supports downloading files and executing arbitrary commands. Finally, for now, anyway, there's Warpwire, a credential harvester that collects passwords and usernames to layer 7 applications (such as RDP) in plain text, and sends them off to a command-and-control server for the snoops to use to gain further access to victims' services and systems. Mandiant has also shared indicators of compromise, so it's worth checking those out, too. And, of course, apply the mitigation before taking off for the weekend.
 github.com
github.com
cross-posted from: https://links.hackliberty.org/post/790988 > DISARM is a framework designed for describing and understanding disinformation incidents. DISARM is part of work on adapting information security (infosec) practices to help track and counter disinformation and other information harms, and is designed to fit existing infosec practices and tools. > > DISARM's style is based on the MITRE ATT&CK framework. STIX templates for DISARM objects are available in the DISARM_CTI repo - these make it easy for DISARM data to be passed between ISAOs and similar bodies using standards like TAXII.
 blog.talosintelligence.com
blog.talosintelligence.com
In cooperation with Dutch Police and Avast, Cisco Talos recovered a decryptor for encrypted files from systems affected by the Babuk ransomware variant known as Tortilla. We first described the operations of Tortilla ransomware in a [blog post in November 2021](https://blog.talosintelligence.com/babuk-exploits-exchange/). Dutch Police used the intelligence provided by Talos to discover and apprehend the actor behind this malware. During the Amsterdam Police operation, Talos obtained and analyzed the decryptor, recovered the decryption key and shared the key with engineers from Avast Threat Labs in charge of development and maintenance of the decryptor for several other Babuk variants. The generic Avast Babuk decryptor was already used as the de facto industry standard Babuk decryptor by many affected users and it made perfect sense to be updated with the keys Talos recovered from the Tortilla decryptor. This way, the users can access programs such as [NoMoreRansom](https://www.nomoreransom.org/en/decryption-tools.html) to download the single decryptor containing all currently known Babuk keys and do not have to choose between competing decryptors for individual variants.
 therecord.media
therecord.media
An official at the Bangladesh Election Commission has claimed that a cyberattack “from Ukraine and Germany” caused an election information app to crash as voters went to the polls on Sunday. There has not been an allegation that the incident affected votes in the country, where incumbent Prime Minister Sheikh Hasina secured her fourth straight term in office after a record low turnout, as [reported](https://www.bbc.co.uk/news/world-asia-67889387) by BBC News. Hasina, who has held power since 2009, is currently the longest-serving female head of government in the world. Her government has faced criticism from the international community, including the [United Nations](https://tbinternet.ohchr.org/_layouts/15/TreatyBodyExternal/Download.aspx?symbolno=CCPR%2fC%2fBGD%2fCO%2f1&Lang=en), amid allegations of human rights abuses and extrajudicial killings. “Her long reign in power has been marked by arrests of opposition leaders, crackdowns on free speech and suppression of dissent,” as Reuters [reported](https://www.reuters.com/world/asia-pacific/bangladesh-pm-hasina-champion-democracy-iron-lady-2024-01-08/). The country’s main opposition, the Bangladesh Nationalist Party (BNP), boycotted the general election on the grounds that the vote would be rigged. BBC News reported that while official figures for Sunday’s vote put turnout at around 40%, critics have claimed even that figure may be inflated. Bangladesh has about 120 million eligible voters. Mohammed Jahangir Alam, the Election Commission’s official secretary, told journalists on Sunday that the election app had been “slowed down from Ukraine and Germany,” without specifying the nature of the cyberattack. “Our team has been working round the clock to fix the issue. Although the app is functioning slowly, it’s still working,” said Alam. The app, [Smart Election Management BD](https://play.google.com/store/apps/details?id=com.electioncommissionsecretariat.sembd&hl=en_US&pli=1), was not essential for voting. It provided “historical and current data on electoral candidates and associate parties” alongside updates on how many votes had been cast. Although not formally confirmed, the incident as described by Alam may have been a distributed denial of service (DDoS) attack — an unsophisticated type of cyber nuisance that works by flooding targeted network resources with junk requests, making them unreachable. The nature of the attack was not disclosed, however it is not possible to spoof the source IP address in an application-layer DDoS that is sending HTTP requests to the target server. Cloudflare, which has historically included Germany and Ukraine among the [largest sources of DDoS traffic](https://blog.cloudflare.com/ddos-attack-trends-for-2021-q4/) — although both accounted for far less traffic than China and the United States — said this “usually indicates the presence of botnets operating from within the country's borders.” ### Allegations of foreign interference Prior to the election, both of the main political parties have made claims and counter-claims about foreign states attempting to influence the vote. Thousands of BNP activists have been arrested following rallies that turned violent, something which the party alleged was instigated by government provocateurs. Arrest warrants are outstanding for many of the party’s senior figures, some of whom live in exile. The BNP accused Russian foreign ministry spokeswoman Maria Zakharova of interference after she claimed that the party’s rallies were being sponsored by the U.S. government in a bid to secure Bangladesh’s support for the U.S. Indo-Pacific strategy. The chief commissioner at the Bangladesh Election Commission has also alleged that “Western nations, including the U.S., are trying to influence the course and results of the general elections in Bangladesh.” Following Sunday’s vote, Andrei Shutoff, a Russian election observer, [reportedly warned](https://organiser.org/2024/01/07/214934/world/if-america-isnt-satisfied-therell-be-attempts-to-destabilise-bangladesh-like-that-of-arab-spring-russian-observer/): “In case the U.S.A. is not satisfied with the results of the people’s vote, attempts to further destabilize the situation in Bangladesh along the lines of the Arab Spring are likely.”
Even as the New Year approached and the world celebrated the festive Christmas season, the cybercriminal community did not pause their activities. Instead, they marked the holiday season in their unique way. On Christmas Eve, Resecurity observed multiple actors on the Dark Web releasing substantial data dumps. These were the result of data breaches and network intrusions to a variety of companies and government agencies. Numerous leaks disseminated in the underground cyber world were tagged with 'Free Leaksmas,' indicating that these significant leaks were shared freely among various cybercriminals as a form of mutual gratitude. Ironically, this display of generosity among cybercriminals is far from a cause for celebration for victims globally. It will inevitably result in them facing a host of adverse effects, such as account takeovers (ATO), business email compromises (BEC), identity theft, and financial fraud. Significantly, the data breaches weren't confined to the United States; they extended globally, impacting individuals in a wide range of countries including France, Peru, Vietnam, Italy, Russia, Mexico, the Philippines, Switzerland, Australia, India, South Africa, and even mixed international sources. This widespread geographical distribution highlights the extensive global reach and severe impact of these cybercriminal activities.  A significant event during the 'Leaksmas' in the Dark Web involved the release of a large dataset from Movistar, a leading telecommunications provider in Peru. This dataset contained over 22 million records, including customers' phone numbers and DNI (Documento Nacional de Identidad) numbers. The DNI, being the sole identity card recognized by the Peruvian Government for all civil, commercial, administrative, and judicial activities, makes its exposure on the Dark Web a serious threat, potentially leading to widespread identity theft and fraud. This incident underscores the critical need for robust Digital Identity Protection programs, particularly in Latin America, where there is an escalating trend of cyber-attacks resulting in major data breaches and significant damages. 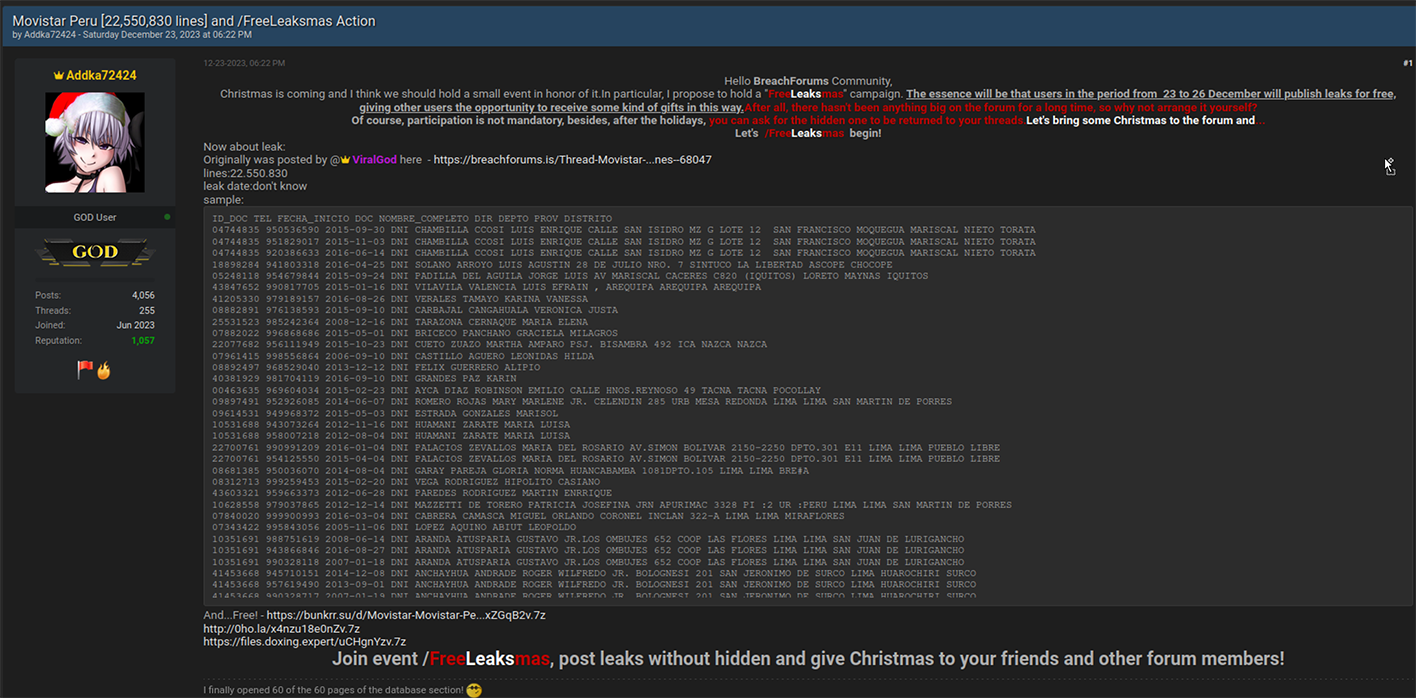 On Christmas, a government agency in Chile experienced a security breach.  In another incident targeting the Asia-Pacific region, cybercriminals released a substantial leak involving one of the major credit services in the Philippines. The perpetrators disclosed over 15.77 GB of data in this breach.  The "Leaksmas" event continued with another significant breach, this time involving a French company. Approximately 1.5 million records from this company were shared freely on the Dark Web. 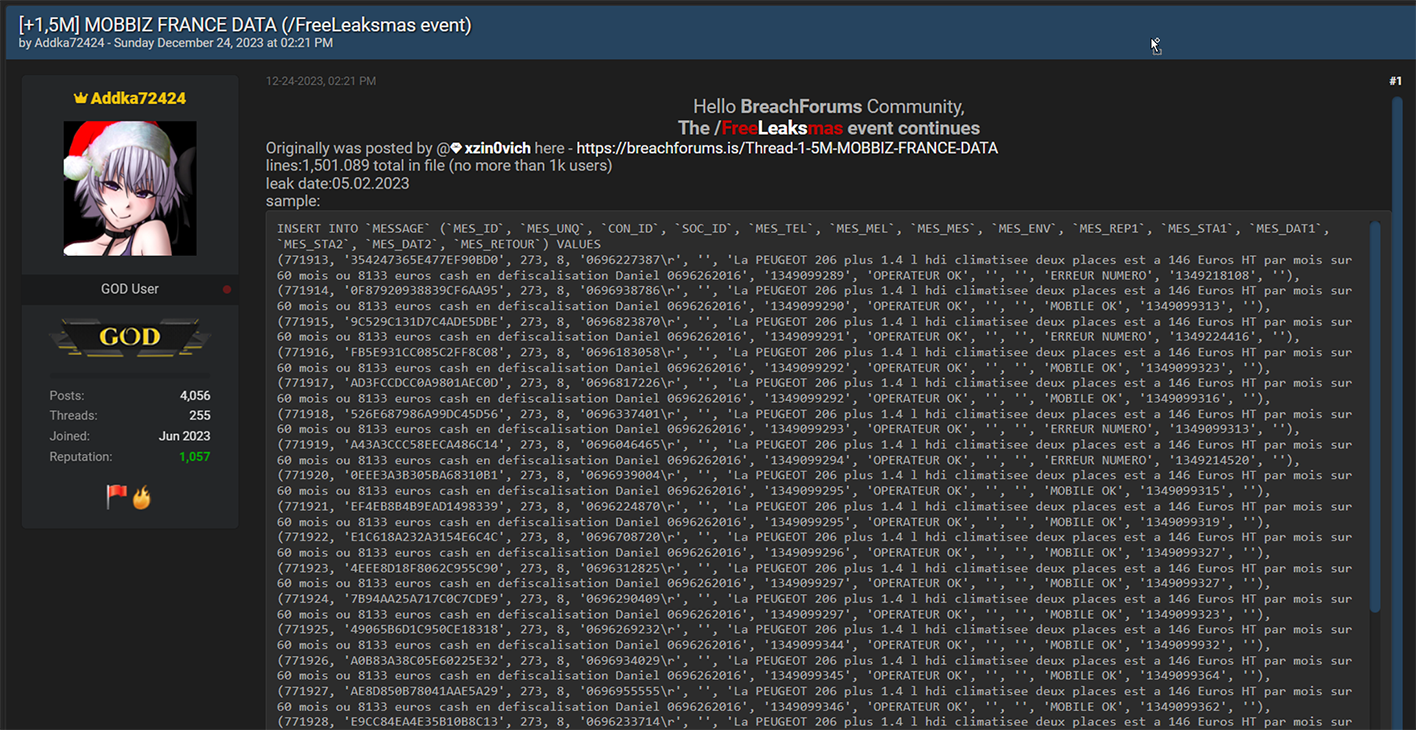 Cybercriminals also "gifted" a leak involving 1.4 million records, associated with a project that was later acquired by Klarna, a Swedish fintech company. Interestingly, rumors of a potential data breach had been circulating since 2022, and several users had received notifications regarding it. However, the complete data dump had not been freely available on the Dark Web until this event. 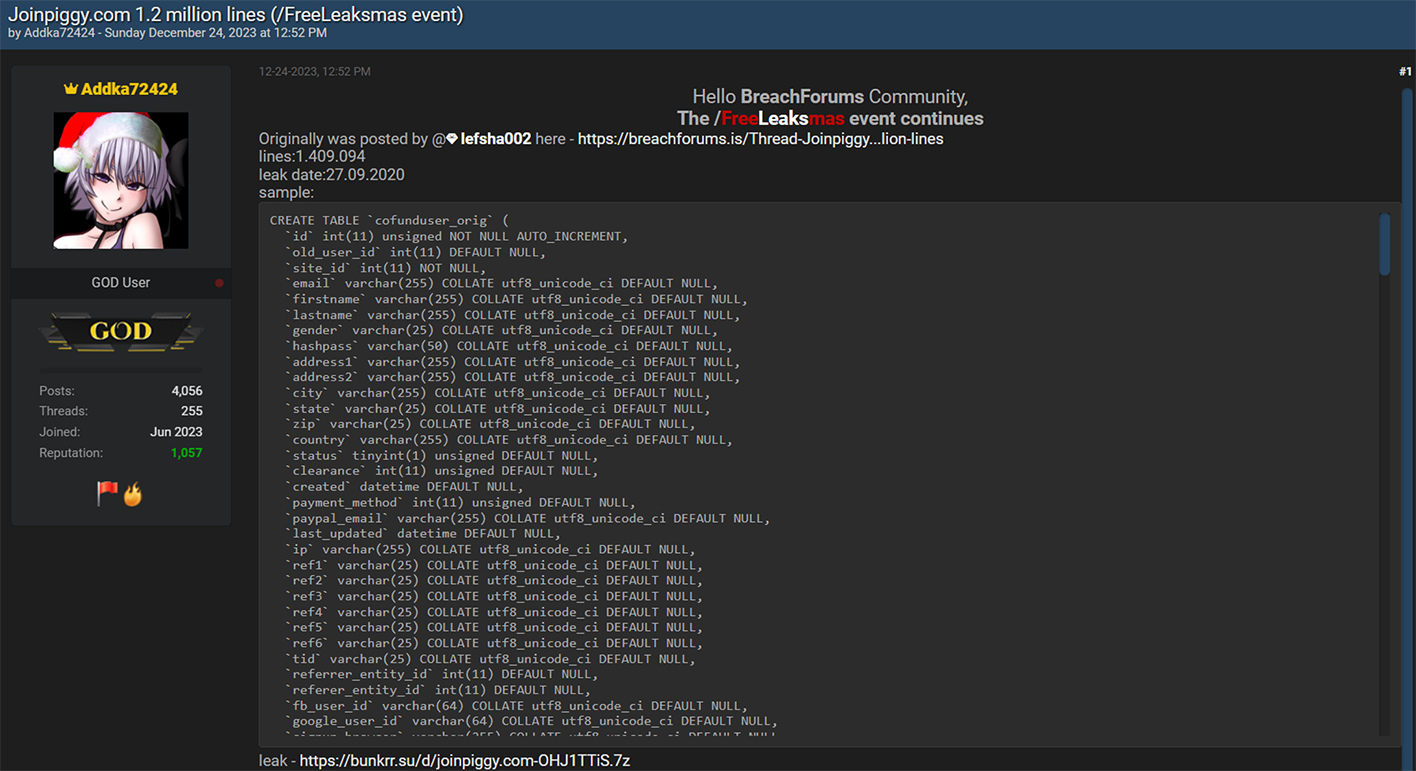 Returning to the Asia-Pacific region, another significant leak that was freely shared on the Dark Web involved a Vietnam-based fashion store. This breach exposed over 2.5 million victim records. Such a database is a valuable asset for spammers and illegal affiliate marketing specialists, offering them the potential to generate substantial profits during the winter holiday season. 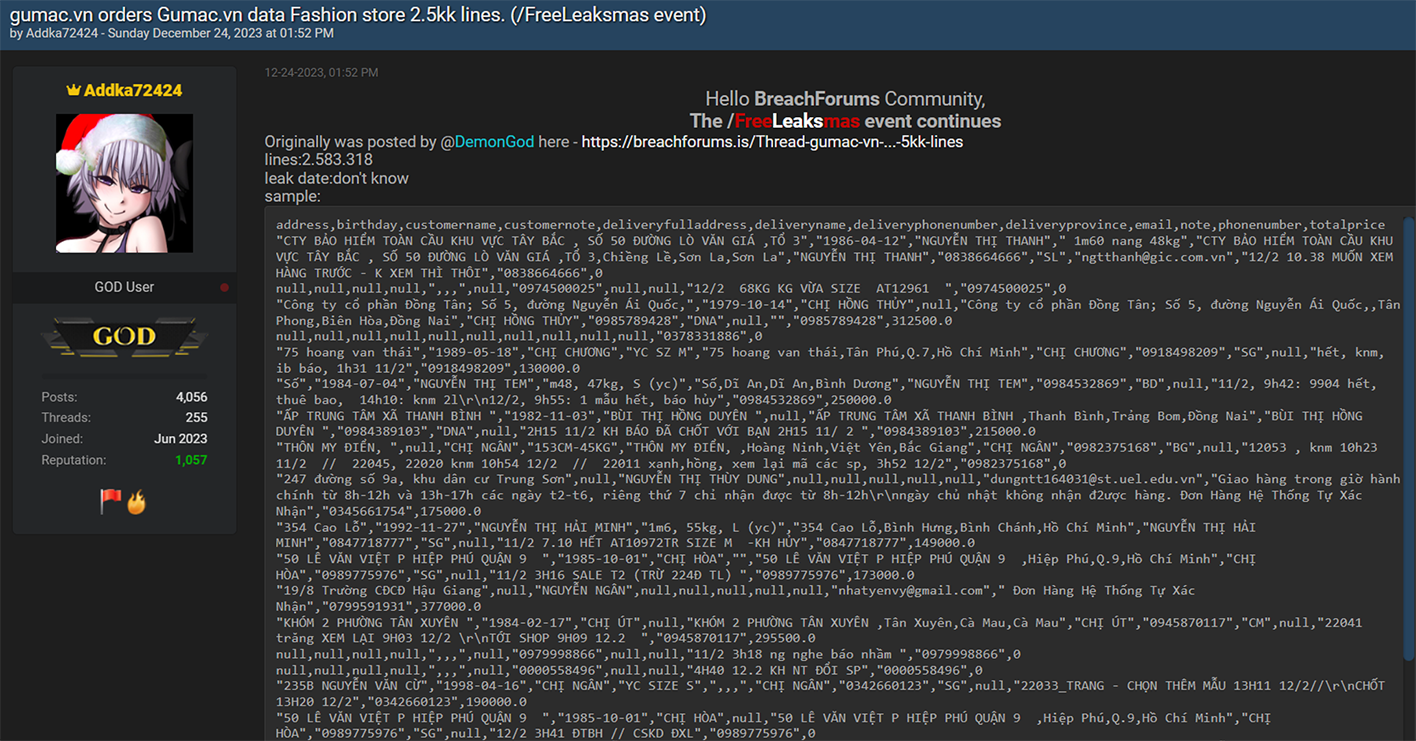 An additional noteworthy leak involved a hacked online military gear shop based in Italy. While the database contained only 2,000 records, the nature of the audience – individuals interested in military gear – makes it particularly attractive to foreign cyber actors, especially those with a focus on defense-related information. 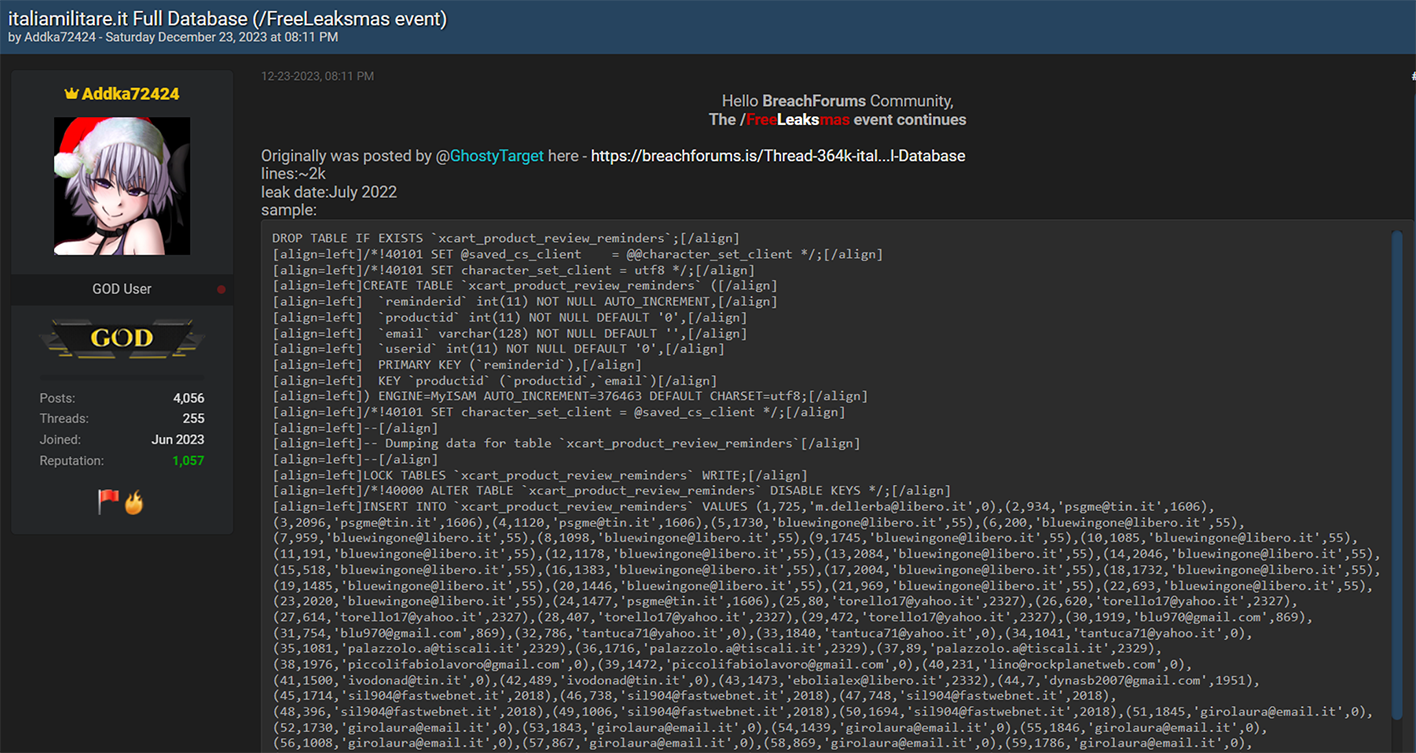 The perpetrators also targeted India, a country known for its vast economy and rapid pace of digitization.  On Christmas, there was a relatively new leak involving a sushi restaurant network from Russia, comprising over 164,052 records. This dataset was notable for not having been previously seen on the Dark Web, making it potentially of particular interest to certain actors. 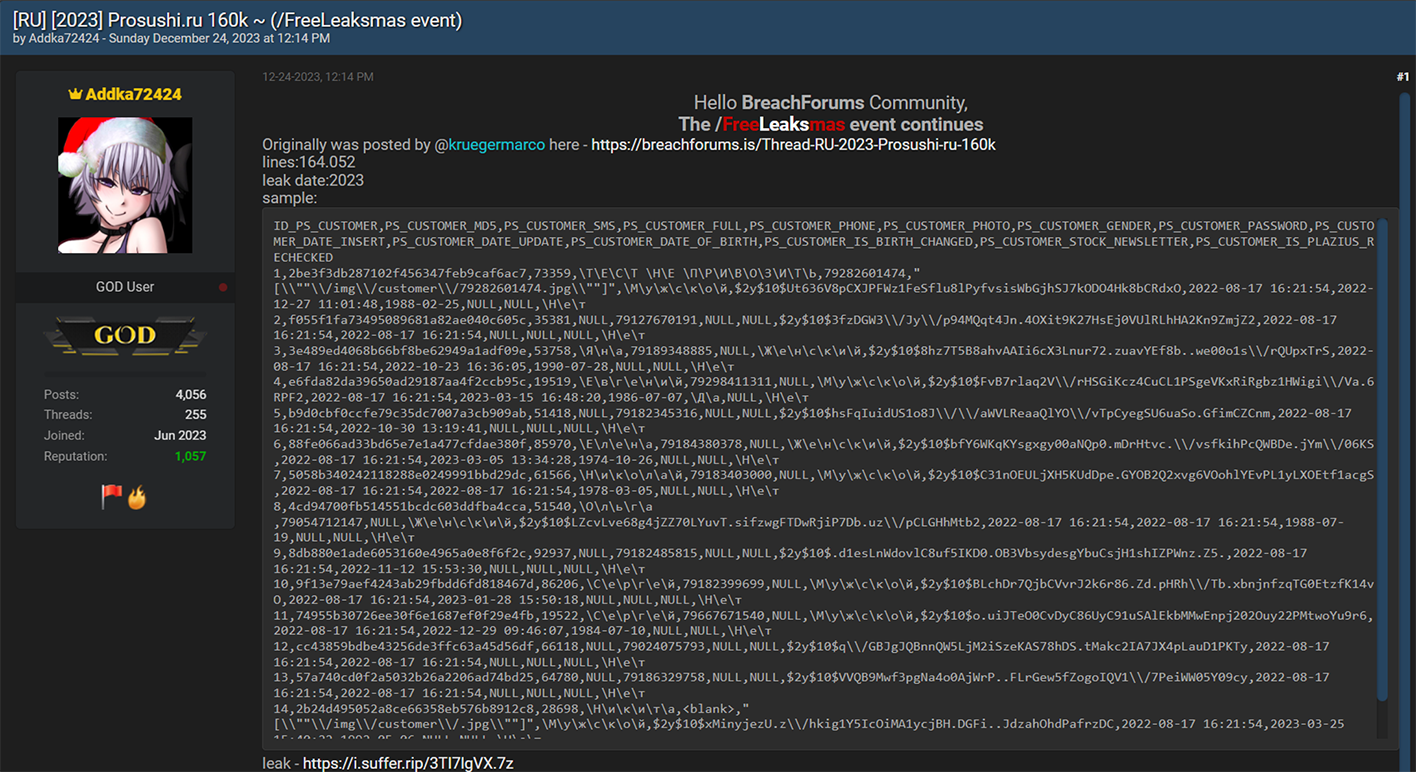 There was a significant leak involving over 2 million records of banking customers from Mexico. It's highly probable that these records were obtained directly from a breached financial institution, a lending provider, or a telemarketing operator that specializes in generating leads for the financial industry. Interestingly, this particular dataset had been previously offered for sale but became freely available during this event. Our assessment suggests that this data might have originated from an older breach, possibly dating back to 2021-2022. Despite its age, the information remains relevant in 2024, as it's unlikely that all the affected individuals would have updated their personal information since the breach. 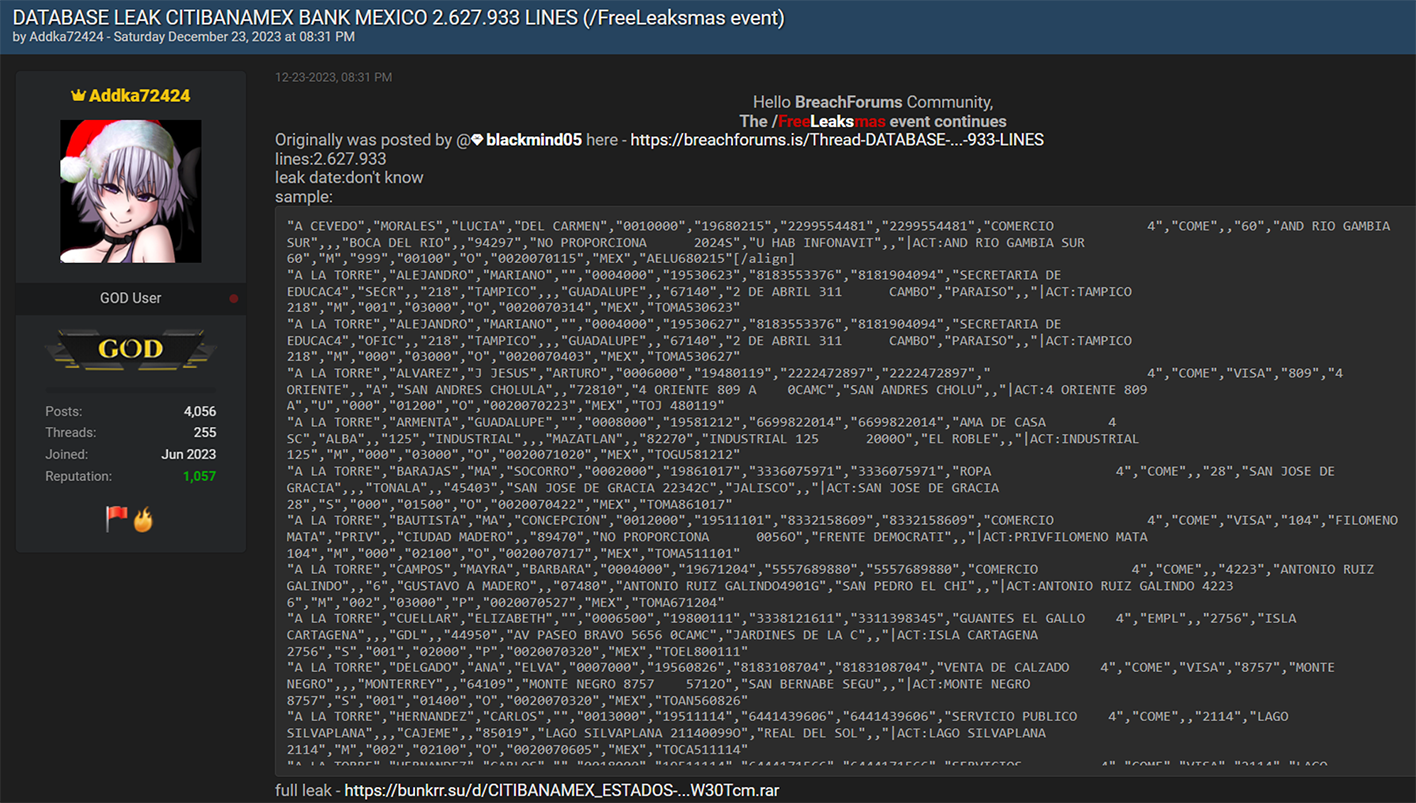 Another significant incident involved a massive data leak from ESSEMTEC.  In addition to these individual leaks, the perpetrators also released larger compilations of data, consisting of multiple separate data breaches. Some of these were extensive packages, known as combo-lists, containing millions of records that included emails and passwords.  **"All I want for Christmas is the destruction of the government."** The most prominent figures in the data leaking activity on the Dark Web during the Christmas period were undoubtedly the actors from SiegedSec. They gained particular notoriety for previously releasing exfiltrated data from the Idaho National Labs. 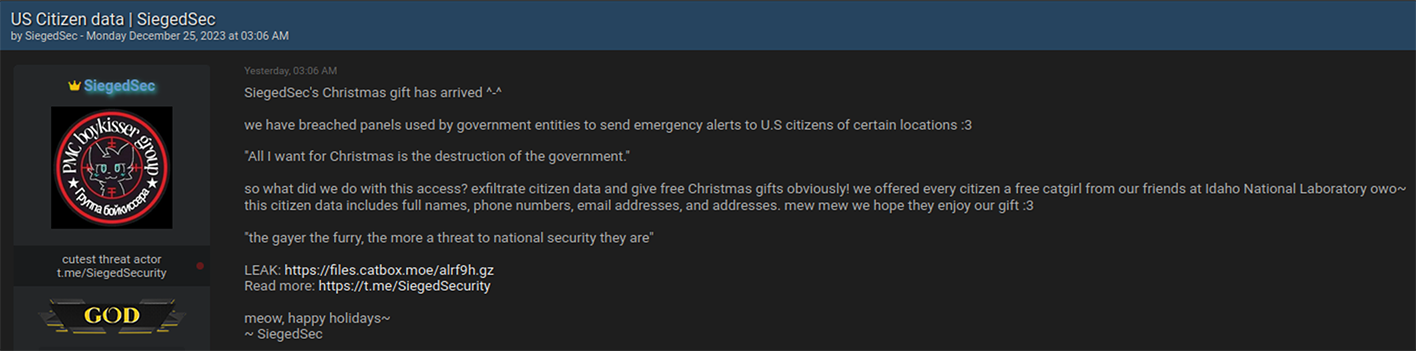 The group SiegedSec has made public claims about successfully hacking into unspecified government resources. Before this, they had celebrated a successful attack on Shufersal, Israel's largest supermarket chain, which they referred to as a “Christmas Gift” in support of Palestine. They also targeted BEZEQ! and Cellcom, one of Israel's leading telecommunications companies. It's worth noting that there have been claims from some groups about ending their associations with SiegedSec due to their stance, but the authenticity of these claims has not been fully verified. 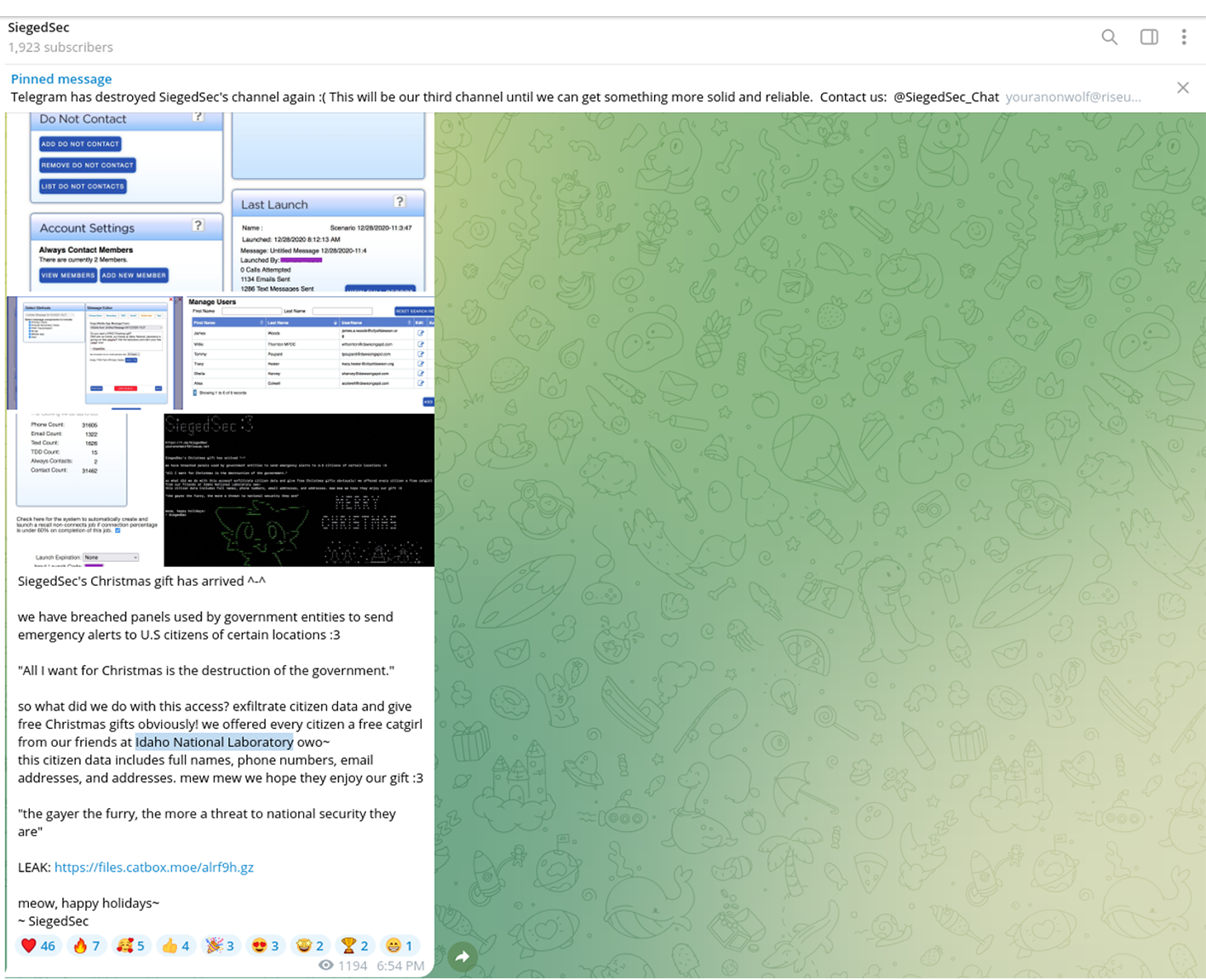 In their Christmas message, SiegedSec mentioned the exfiltration of citizen data, suggesting that we can anticipate more unexpected actions from them in the upcoming year.  cont...
 therecord.media
therecord.media
 The Google-owned cybersecurity firm Mandiant said it is looking into an incident where its X account was taken over by someone sharing links to a cryptocurrency platform. On Wednesday afternoon around 3:30 pm EST, Mandiant’s account on the social media platform tweeted out links to a company called Phantom, which offers customers a wallet for cryptocurrency. The account appeared to have been deleted for several minutes before returning with Mandiant logos but its username changed to “@phantomsolw.” As of 5:30 p.m. EST, the account has retweeted dozens of messages sent out by Phantom. “We are aware of the incident impacting the Mandiant X account and are working to resolve the issue,” a Mandiant spokesperson told Recorded Future News. Representatives for Phantom did not respond to requests for comment. The company’s wallet is widely regarded and available on the app stores for both Google and Apple. Mandiant was [purchased](https://cloud.google.com/blog/products/identity-security/google-completes-acquisition-of-mandiant) by Google in 2022 for $5.3 billion and incorporated into Google Cloud. In recent months, concerns have grown over X’s ability to protect high-profile accounts from takeovers. Since being purchased by Tesla CEO Elon Musk, the social media site has cut hundreds of security employees, exposing it to a wave of spam accounts. On Tuesday, a Canadian senator had their [Twitter account taken over](https://twitter.com/malwrhunterteam/status/1742294268075458617) to spread a scam. Last month, two researchers [discovered](https://twitter.com/shoucccc/status/1734684850173739412) vulnerabilities in Twitter that were [not addressed](https://twitter.com/rabbit_2333/status/1734881873099379189) for weeks by the social media site’s team. Chaofan Shou, a Ph.D. student at the University of California - Berkeley, told Recorded Future News that the company never replied to his email about the issue. In a post on the platform, he said the bugs would allow anyone to take over an account. “Both vulnerabilities are obvious and easy to find for folks working in security,” he said on December 13. “The exploit I disclosed is built up on two vulnerabilities. One discovered by @rabbit_2333 and one discovered by me. Twitter has acknowledged neither of them.”
 therecord.media
therecord.media
The owner of an apartment in Veliky Novgorod in Russia has been arrested for discrediting the country’s armed forces after a neighbor alerted the police to the message ‘Slava Ukraini’ scrolling across their LED curtains. When police went to the scene, they saw the garland which the owner had hung in celebration of the New Year and a “slogan glorifying the Armed Forces of Ukraine,” as a spokesperson for the Ministry of Internal Affairs told state-owned news agency [TASS](https://tass.ru/proisshestviya/19665075). The apartment owner said the garland was supposed to display a “Happy New Year” greeting, TASS reported. Several other people in Russia [described](https://community.alexgyver.ru/threads/wifi-lampa-budilnik-obsuzhdenie-proshivki-fieryledlamp-ot-alvikskor-perevod-mishanyats.7530/page-38#post-158994) a similar experience on the AlexGyver web forum, linked to a DIY blog popular in the country. They said at the stroke of midnight on New Year’s Eve, their LED curtains also began to show the “Glory to Ukraine” message in Ukrainian. It is not clear whether any of these other posters were also arrested. The man in Veliky Novgorod will have to defend his case in court, according to TASS. Police have seized the curtain itself. An independent investigation into the cause of the message by the AlexGyver forum users found that affected curtains all used the same open-source firmware code. The original code appears to have originated in Ukraine before someone created a fork translated into Russian. According to the [Telegram channel](https://t.me/alexgyvershow/482) for AlexGyver, the code had been added to the original project on October 18, and then in December the people or person running the fork copied and pasted that update into their own version. “Everyone who downloaded and updated the firmware in December received a gift,” the Telegram channel wrote. The message was “really encrypted, hidden from the ‘reader’ of the code, and is displayed on the first day of the year exclusively for residents of Russia by [geographic region].” Oleg Shakirov, an independent Russian cyber policy researcher, compared on [social media](https://twitter.com/shakirov2036/status/1742553600495124872) the LED incident to other examples of open-source software manipulation within the context of protesting the invasion of Ukraine. These included an intentional amendment to the JavaScript library node-ipc that checked to see if its host machine used an IP address based in Russia or Belarus, and if it did write over all of the device’s files with a heart symbol, as [reported](https://www.theregister.com/2022/03/18/protestware_javascript_node_ipc/) by The Register. Beyond the consequences for the arrested man, the LED prank is unlikely to be remembered as one of the more significant cyber actions of the war between Russia and Ukraine, although it highlights the potential vulnerabilities caused by software dependencies. Last month, an [investigation](https://www.radiosvoboda.org/a/skhemy-kamery-sposterezhennya-trassir-kreml/32718775.html) by Radio Free Europe reported that Russia's intelligence services might have been obtaining video footage from thousands of Ukrainian surveillance cameras equipped with a Russian software program known as Trassir. On Tuesday, Ukraine’s security officers said they took down two online surveillance cameras that were [allegedly hacked](https://therecord.media/ukraine-says-russia-hacked-web-cameras-to-spy-on-kyiv-targets) by Russia to spy on air defense forces and critical infrastructure in Ukraine’s capital, Kyiv. Numerous supply chain attacks have been observed during the course of the conflict, with Google’s Mandiant unit last year warning that hackers had been targeting Ukrainian government networks using fake Windows installers. In March of last year, Rosaviatsia — responsible for regulating civil aviation in Russia — reportedly had to switch to [pen and paper](https://t.me/aviatorshina/2160) after a reported supply-chain attack, resulting in the collapse of its entire network and the loss of more than a year’s worth of emails. The agency denied the reports.
 therecord.media
therecord.media
Crypto platform Orbit Chain said it is working with the Korean National Police Agency and Korea Internet & Security Agency (KISA) to address a cyberattack that led to the theft of more than $81 million worth of cryptocurrency. On the night of New Years Eve, Orbit Chain confirmed that they began to see unauthorized transactions on their platform involving several cryptocurrencies including U.S.-dollar-pegged coins USDC and USDT as well as ETH and others. Orbit Chain’s platform supports communication between different blockchain networks. The company [hired](https://twitter.com/ChainLight_io/status/1741658031363158419) blockchain security company ChainLight to lead the investigation. Other blockchain research companies, including [CertiK](https://twitter.com/CertiKAlert/status/1741616306531561593) and [PeckShield](https://twitter.com/peckshield/status/1741613040335036513), pegged the losses at around $81.5 million, with $30 million taken in USDT and $10 million in USDC. “Orbit Chain team has developed a system for investigation support and cause analysis with the Korean National Police Agency and KISA (Korea Internet & Security Agency), enabling a more proactive and comprehensive investigation approach. Furthermore, we are also discussing close cooperation with domestic and foreign law enforcement agencies,” they [said](https://twitter.com/Orbit_Chain/status/1742132887301107780) in a notice on Tuesday. “In order to resolve this issue, the Orbit Chain team will utilize all available methods to track down the hackers and recover the funds. We sincerely request that all members of the Orbit Chain community and the Web3 ecosystem help spread this information as widely as possible.” They asked other global cryptocurrency exchanges to freeze the stolen assets and warned customers to be wary of scams related to potential repayment of lost funds. The company noted that it has tried to communicate with the attackers, sending them multiple messages on Monday. It is unclear if the hackers have responded, and the company did not respond to requests for comment about their communications with those behind the incident. Orbit Chain, which is based in South Korea, [added](https://twitter.com/Orbit_Chain/status/1741846105149821166) that it is looking into the possibility that the attack was launched by hackers based in North Korea — whose government has been implicated in dozens of the largest crypto thefts over the last three years. PeckShield [noted](https://twitter.com/PeckShieldAlert/status/1741852326305100283) that including the funds stolen from Orbit Chain, nearly $100 million was taken from crypto platforms in December 2023. U.S. officials [say North Korean hackers](https://therecord.media/us-treasury-sanctions-sinbad-crypto-mixer) have stolen over $2 billion worth of cryptocurrency to help fund the North Korean government’s activities — including its weapons of mass destruction and ballistic missile programs.
 therecord.media
therecord.media
Ukraine’s security officers said they took down two online surveillance cameras that were allegedly hacked by Russia to spy on air defense forces and critical infrastructure in Ukraine’s capital, Kyiv. The cameras were installed on residential buildings in Kyiv and were initially used by residents to monitor the surrounding area and parking lot. After hacking them, the Russian intelligence services supposedly gained remote access to the cameras, changed their viewing angles, and connected them to YouTube to stream sensitive footage. According to Ukraine’s security service, SBU, this footage likely [helped](https://t.me/SBUkr/10757) Russians direct drones and missiles toward Kyiv during a large-scale [missile strike](https://therecord.media/missile-strikes-disrupt-internet-and-power-in-kyiv) against Ukraine on Tuesday. During the attack, Russia fired almost 100 drones and missiles, primarily targeting Kyiv and Kharkiv, Ukraine’s second-largest city. At least 5 people were killed, and 129 were injured. Since Russia invaded Ukraine in February 2022, the SBU said it has blocked about 10,000 digital security cameras that Moscow might have used to prepare for missile strikes on Ukraine. According to the [investigation](https://www.radiosvoboda.org/a/skhemy-kamery-sposterezhennya-trassir-kreml/32718775.html) by Radio Free Europe, Russia's intelligence services might have been getting video footage from thousands of Ukrainian surveillance cameras equipped with a Russian software program known as Trassir. This surveillance system can capture the movements of people and vehicles and is capable of recognizing faces and license plates. The journalists found that the footage from those cameras went directly to servers in Moscow and could likely be accessed by Russia’s security services. Ukraine started to abandon Russian software only after the start of the invasion. Online footage, including photos and videos, could be a valuable source of information for both Ukrainian and Russian intelligence agencies. Ukrainian laws prohibit citizens from sharing photos or videos of residential buildings or critical infrastructure objects hit by Russians during missile strikes, as it helps the enemy forces to “correct” their targeting. The penalty for this offense is a potential prison term of up to 12 years. The SBU called on the owners of street surveillance cameras to stop online broadcasts from their devices and to report any detected streams from such cameras on YouTube.
 therecord.media
therecord.media
A voice over internet protocol (VoIP) service provider charged with sending billions of illegal robocalls was issued a $10 million penalty and is banned from supporting certain telemarketing practices as part of a settlement, the Federal Trade Commission (FTC) and Department of Justice (DOJ) announced Tuesday. XCast Labs was accused of allowing the robocalls to flow through its network and ignoring multiple warnings — beginning in January 2020 — to stop the practice. The behavior violates the FTC’s Telemarketing Sales Rule, which mandates telemarketers disclose who they are, bars misrepresentations and blocks calls to consumers listed on the federal Do Not Call (DNC) registry. Tuesday’s [court order](https://www.documentcloud.org/documents/24251982-ecf38-stipulated-order-xcastlabs), issued through the U.S. District Court for the Central District of California, also imposed the $10 million fine, which has been put on hold because XCast Labs can’t pay it. The company is also required to take steps to comply with telemarketing laws, including setting up additional screening of customers and transmissions to better police illegal robocalls. Some of the robocalls that XCast Labs was accused of facilitating involved scams from companies pretending to be government agencies, according to the [May complaint](https://www.documentcloud.org/documents/24251974-2223097-xcast-labs-inc-complaint-for-permanent-injunction). For example, some of the calls claimed to be from the Social Security Administration and warned that utility services like heat and water would be cut off unless payments were made, the complaint said. Other calls told consumers to act quickly to reverse made up credit card charges. The robocalls featured prerecorded marketing messages, many of which were sent to DNC-registered phone numbers, the complaint said. The illegal calls began in at least January 2018, according to the complaint, which said some of the calls marketed goods and services with a “history of deceptive sales practices,” including extended warranties for cars. Even calls that did not fraudulently purport to be from the government did not “truthfully identify” the seller, the DOJ [press release said](https://www.justice.gov/opa/pr/united-states-settles-suit-against-telecommunications-service-provider-assisting-and). Instead, those calls included “false or misleading statements to induce purchases or were transmitted with ‘spoofed’ caller ID information.” XCast kept extensive records of its transmissions, including the exact date and time of a call, the phone numbers involved and exact durations of the calls. The FTC said records produced for just three of XCast Labs’ customers showed almost two billion of the robocalls were sent to numbers included on the DNC Registry. The FTC warned other robocallers to take notice. “XCast was warned several times that illegal robocallers were using its services and did nothing,” Director Samuel Levine of the FTC’s Bureau of Consumer Protection said in a prepared [statement](https://www.ftc.gov/news-events/news/press-releases/2024/01/xcast-labs-will-be-banned-supporting-illegal-telemarketing-practices-settle-ftc-charges-it-assisted). “Companies that turn a blind eye to illegal robocalling should expect to hear from the FTC.”
 www.theregister.com
www.theregister.com
Security researchers say info-stealing malware can still access victims' compromised Google accounts even after passwords have been changed. A zero-day exploit of Google account security was first teased by a cybercriminal known as "PRISMA" in October 2023, boasting that the technique could be used to log back into a victim's account even after the password is changed. It can also be used to generate new session tokens to regain access to victims' emails, cloud storage, and more as necessary. Since then, developers of info-stealer malware – primarily targeting Windows, it seems – have steadily implemented the exploit in their code. The total number of known malware families that abuse the vulnerability stands at six, including Lumma and Rhadamanthys, while Eternity Stealer is also working on an update to release in the near future. They're called info stealers because once they're running on some poor sap's computer, they go to work finding sensitive information – such as remote desktop credentials, website cookies, and cryptowallets - on the local host and leaking them to remote servers run by miscreants. Eggheads at CloudSEK say they found the root of the exploit to be in the undocumented Google OAuth endpoint "MultiLogin." The exploit revolves around stealing victims' session tokens. That is to say, malware first infects a person's PC – typically via a malicious spam or a dodgy download, etc – and then scours the machine for, among other things, web browser session cookies that can be used to log into accounts. Session cookies ideally expire frequently, something that can limit their usefulness in account takeover attacks. However, recent cases such as Okta's in October, which involved the theft of HAR files that often contain session cookies, have demonstrated that session hijackings are entirely practical and can lead to major security incidents. Those session tokens are then exfiltrated to the malware's operators to enter and hijack those accounts. It turns out that these tokens can still be used to login even if the user realizes they've been compromised and change their Google password. It appears users should log out entirely, and thus invalidate their session tokens, to prevent exploitation. MultiLogin is responsible for synchronizing Google accounts across different services. It accepts a vector of account IDs and auth-login tokens to manage simultaneous sessions or switch between user profiles. Reverse engineering the info-stealer malware revealed that the account IDs and auth-login tokens from logged-in Google accounts are taken from the token_service table of WebData in Chrome. This table contains two columns crucial to the exploit's functionality: service (contains a GAIA ID) and encrypted_token. The latter is decrypted using a key stored in Chrome's Local State file, which resides in the UserData directory. The stolen token:GAIA ID pairs can then be used together with MultiLogin to continually regenerate Google service cookies even after passwords have been reset, and those can be used to log in. Pavan Karthick M, threat intelligence researcher at CloudSEK, reckons the discovery provides evidence of cybercriminals' high degree of sophistication. In Lumma's case, each token:GAIA ID pair is encrypted by the malware, masking the finer details of the mechanism. In a more recent update, however, Lumma introduced SOCKS proxies to bypass Google's IP-based restrictions on token regeneration. In doing so, the malware's developers now expose some details of the requests and responses, potentially undoing some of their earlier efforts to conceal the functionality's inner workings. The encryption of the traffic between the malware's C2 and MultiLogin also lessens the chances of standard security measures detecting the malicious activity, Karthick said, since encrypted traffic is more likely to be overlooked. "The tactical decision to encrypt the exploit's key component showcases a deliberate move towards more advanced, stealth-oriented cyber threats," he added. "It signifies a shift in the landscape of malware development, where the emphasis is increasingly on the concealment and protection of exploit methodologies, as much as on the effectiveness of the exploits themselves."
 media.ccc.de
media.ccc.de
Imagine discovering a zero-click attack targeting Apple mobile devices of your colleagues and managing to capture all the stages of the attack. That’s exactly what happened to us! This led to the fixing of four zero-day vulnerabilities and discovering of a previously unknown and highly sophisticated spyware that had been around for years without anyone noticing. We call it Operation Triangulation. We've been teasing this story for almost six months, while thoroughly analyzing every stage of the attack. Now, for the first time, we're ready to tell you all about it. This is the story of the most sophisticated attack chain and spyware ever discovered by Kaspersky. In this presentation, we will share: * How we managed to discover and capture all stages of a zero-click attack on iOS, despite the attackers’ efforts to hide and protect it, * a comprehensive analysis of the entire attack chain, which exploited five vulnerabilities, including four zero-days * the capabilities of the malware that transforms your phone into the ultimate surveillance tool, * and the links to previously known malware we were able to find.
 www.theregister.com
www.theregister.com
Kaspersky's Global Research and Analysis Team (GReAT) has exposed a previously unknown "feature" in Apple iPhones that allowed malware to bypass hardware-based memory protection. Addressed as [CVE-2023-38606](https://www.theregister.com/2023/07/25/apples_pushes_patches/), which was patched in July 2023, the issue affected iPhones running iOS versions up to 16.6, [according](https://www.kaspersky.com/about/press-releases/2023_kaspersky-discloses-iphone-hardware-feature-vital-in-operation-triangulation-case) to the cybersecurity outfit this week. Kaspersky reckons the hardware feature ([technical details here](https://securelist.com/operation-triangulation-the-last-hardware-mystery/111669/)) may have been intended for testing or debugging. Yeah, hopefully that. Certainly, the GReAT gang couldn't find any public documentation on it, which meant the attack vector proved tricky to detect and analyze using the team's usual tools when miscreants came to exploit the hole. According to Kaspersky, "attackers leveraged this hardware feature to bypass hardware-based security protections and manipulate the contents of protected memory regions." Researchers had to reverse-engineer the device to track down the vulnerability exploited. Particular attention was paid to Memory-Mapped IO (MMIO) addresses used for communication between the CPU and other devices. The problem was that the attackers used unknown MMIO addresses to bypass hardware-based kernel protection. Therefore, the team had to pick through the hardware, firmware, and kernel images to work out what was going on. "This is no ordinary vulnerability," said Boris Larin, Principal Security Researcher at Kaspersky's GReAT. "Due to the closed nature of the iOS ecosystem, the discovery process was both challenging and time-consuming, requiring a comprehensive understanding of both hardware and software architectures. What this discovery teaches us once again is that even advanced hardware-based protections can be rendered ineffective in the face of a sophisticated attacker, particularly when there are hardware features allowing to bypass these protections." The vulnerability played a critical role in the ["Operation Triangulation" campaign](https://www.theregister.com/2023/06/21/apple_patches_triangledb_spyware/) earlier this year, which allowed miscreants to gain access to targeted devices, deploy spyware, and snoop user data. Kaspersky informed Apple about the exploitation of the hardware feature, which was swiftly mitigated. However, as Larin observed, all the hardware protections in the world won't help if somebody leaves in an undocumented something that allows those protections to be bypassed. 'Security through obscurity' just doesn't cut it anymore.
 therecord.media
therecord.media
Researchers have discovered a new cyber operation against Ukrainian and Polish organizations, attributing it to the Russian state-controlled hacker group known as Fancy Bear. During the attacks in December, Russian hackers sent phishing emails to their victims with malicious attachments. Once opened, these attachments infected targeted devices with the novel Masepie malware, according to [a report](https://cert.gov.ua/article/6276894) from Ukraine’s computer emergency response team (CERT-UA). The malware, written in the Python programming language, can upload files and execute commands, researchers said. In the latest campaign, the hackers used it to upload data-stealing malware called Steelhook, which targets web browsers, and a backdoor called Oceanmap, which leverages email software. After the initial compromise, hackers also integrate open-source tools like Impacket and Smbexec into the system to perform reconnaissance. These tools are commonly used in penetration testing and ethical hacking to understand and exploit network vulnerabilities. However, they could also be misused by hackers for malicious purposes. Researchers said that the hackers' goal in this campaign was not to infect just one computer but to expand the attack to the entire network of the organization. In Ukraine, the group’s victims included unnamed government agencies. Poland’s cyber agency hasn’t responded to a request for comment. In 2023 alone, Fancy Bear, also known as APT28, targeted Ukrainian [energy facilities](https://therecord.media/ukraine-energy-facility-cyberattack-fancy-bear-email), government agencies, and [the military](https://therecord.media/russia-fancy-bear-hackers-targeted-ukraine). France also [accused](https://therecord.media/france-russia-fancybear-apt28-government-universities-think-tanks-espionage) the hackers of spying on French universities, businesses and think tanks. The group is linked to Russia’s military intelligence agency (GRU) and primarily attacks government, energy, transportation and nongovernmental organizations in the U.S., Europe, and the Middle East. The hackers commonly exploit publicly available vulnerabilities such as [Microsoft Outlook flaws](https://therecord.media/unpatched-microsoft-outlook-email-attacks-fancy-bear) or a popular file archiver utility for Windows called [WinRAR](https://therecord.media/russia-china-hackers-exploit-winrar-bug). Earlier in December, the Polish cybersecurity agency said that Fancy Bear exploited the Microsoft Outlook vulnerability to gain access to mailboxes containing “high-value information.”
 web.archive.org
web.archive.org
When AlphV/BlackCat's website went dark this month, it was like Chrimbo came early for cybersecurity defenders, some of whom seemingly believed law enforcement had busted one of the most menacing cyber criminal crews. The excitement lasted just five days, though, and its website is now back online, albeit in worse shape than before. New victims are already being posted to the site. Regardless, many are skeptical of the ransomware group's explanation that a "hardware fault" was to blame, and rumors that police infiltrated the ring are still wafting throughout the industry. Though it happens rarely, it's always a good day when a ransomware group is taken down by law enforcement. Rarer still is a takedown where one gets a detailed look at the methods that were used in these infiltrations. Singapore-based Group-IB celebrated its 20th anniversary in the cybersecurity industry this year, and during this time its researchers have broken into an array of ransomware groups and their affiliates. The full number remains a secret. Before the authorities got their hands on Hive at the start of this year, Group-IB's researchers were inside as early as 2021, tricking their affiliates into accepting them, learning how they operated, and ultimately gathering the kind of information usually reserved for insiders only. In 2023 alone, the serial intruders have infiltrated affiliates from Qilin and farnetwork, and over the past few years there have been many more to add to that list, though the details of which have scarcely been made public. Group-IB's threat intelligence team spoke to The Register about how they're able to consistently break into cybercriminals' ranks and the vast work that goes into each operation. Four-step foundation The initial infiltration, Group-IB says, can be broken down into four key stages all connected by the common theme of gathering as much information about the ransomware-as-a-service (RaaS) group as possible. "First, the team is gathering intel about a specific RaaS of interest. Certain RaaS programs, such as Qilin and Hive, are very private and close, hence it's important to learn about it as much as you can before you engage with the threat actor. "Consequently, threat intelligence specialists start looking for RaaS programs' terms and conditions for affiliates, entry prerequisites, etc. Any valuable information we could use during the interview stage. "Then the team starts obtaining contact information for the ransomware manager associated with the targeted RaaS program and attempts to establish communication with them. The most intricate phase is the interview typically facilitated through encrypted messengers." All of this sets up the researchers for the later stages of the intrusion, and having a deep understanding of how the criminals operate proves especially useful during the interview if the target group has a particularly stringent vetting process, though this isn't always the case. Some groups will spend time assessing each candidate for their RaaS program, including their technical expertise and grasp of specific terms, while others will simply grant access to an affiliate program seemingly with little to no thought. It's generally understood, by the good guys and the bad, that the cybercrime underworld is teeming with researchers trying to unearth secrets from ransomware groups and as a result, it's becoming a vastly more difficult feat to infiltrate them. The interview Getting to the interview stage is the next step in the intrusion and where the quality of the research into the group will determine the success of the operation. Questions will typically revolve around the candidate's prior experience with attacking organizations, which is where the preparation shines. RaaS managers will quiz potential affiliates on the ransomware landscape generally, and how other groups operate, discussing unconventional tactics, techniques, and procedures, the researchers say. They'll also ask about the candidate's own experience in attacking organizations – light work for researchers whose job it is to analyze exactly how attacks unfold day in, day out. It's a case of taking an incident they examined recently and reciting it to pass themselves off as a genuine bad guy. Just like any other employer, RaaS groups will also do their due diligence as regards a candidate's character, as well as their capability. Group-IB says it's important to apply for affiliate positions through conversations on cybercrime forums, using accounts that have been developed for years, given they operate in a landscape where infiltration attempts are rife. Using mature accounts that appear to be genuine members of, and active participants in, the cybercrime community is vital in dampening suspicions of foul play. The team isn't willing to discuss with us the specifics of how to make an account seem genuine, through fear of jeopardizing future intrusion attempts. We're told they're being as genuine as can be, but will naturally be holding some details back. It requires a great deal of leg work just to make sure the intruders appear genuine online, in the digital realm, but doing so in the actual interview, without giving oneself away, is another challenge entirely. Communication here is crucial. Unlike Brad Pitt's Basterds in Tarantino's masterpiece of a Nazi tavern scene, the researchers understand that native speakers can flush out a foreigner with ease. One slip of the tongue or misused turn of phrase can make the difference in the operation's success. A diverse team is a successful one. "The most challenging part is to establish trust without arousing suspicion," the researchers say. One of the less straightforward methods RaaS managers use is to evaluate the candidate's use of language. They'll specifically look at the nuances in their communication, such as idioms, that could suggest they're not native speakers from whichever country they claim to be. Group-IB's threat intelligence unit is blessed with proficient speakers in Chinese, English, Arabic, Russian, Turkish, Hindi, Dutch, French, Spanish, Thai, and "many other languages" to help them bypass this filter. Predictably, a candidate will also be expected to demonstrate their technical understanding of how to carry out an attack, including their knowledge of the different tools they use. Access granted, and the timer begins Passing the interview stage is the biggest hurdle to surmount and once that's done and a base level of trust is earned, the real intel-gathering can begin. During previous infiltrations, the Group-IB team has published various revelations about the world's top ransomware gangs. With Hive, it was able to identify the exact number of attacks as well as make an educated assumption about the number of companies that paid their ransom demands to keep their data confidential. The farnetwork case revealed the group's payment structure and policy around initial intrusions into victims' networks. The Qilin operation also revealed a lucrative payment structure, as well as an inside look at how affiliates build their custom ransomware payload using the group's builder. However, there is a limit on what can be achieved before the lack of criminality will be spotted and the researchers are rumbled. If it ever got to the point where they had to "prove themselves" to keep a degree of trust, by carrying out an attack or any other illegal act, the researchers are staunch in their position that the operation would end there. "It's important to emphasize that as a threat intelligence analyst, you should strictly refrain from any illegal methods," they say. "Your primary objective is to obtain as much information about the victim to mitigate further damage. For example, during the interview with farnetwork, we were provided a set of compromised credentials. We established the victims, found the source of the breach, and sent the notification to the affected company. "It is essential to operate within the confines of the law. If security researchers engage in unlawful activities to catch a 'big fish,' they become indistinguishable from cybercriminals themselves." Value of the operation When illegality is out of the question, these operations have an inherently limited shelf life. Researchers who can't ever fully earn the trust of criminals by becoming one of them will never secure the long-term access to a RaaS group that's required to understand how it operates on a deep level. Which raises the question: What use is such an endeavor? Is it worth the outlay of resources? Group-IB says it absolutely is. As demonstrated during previous encounters, insiders can help victims manage their incidents by alerting them to what the attacker has stolen, even if the attack itself can't at that point be reversed. These infiltrations also provide defenders with information that can help inform a wide range of investigative activities down the line and support industry-wide mitigation efforts. "Such information helps understand the specific capabilities of gangs' builders, how malicious actors make payments to group owners, what manuals RaaS owners provide to affiliates, and track malicious infrastructure," its threat intel team says. "These insights not only aid cybercrime investigations but also enhance our incident response capabilities as we are able to analyze new malware samples, gather Indicators of Compromise, and valuable information for threat attribution. This ultimately helps us to better understand how to protect our customers against the threat of ransomware." However, as the Group-IB mentioned earlier, none of this would be possible without a team – "you simply cannot do it alone," they say. Being able to rely on a bank of intelligence, years of combined experience, and, in the case of the interview, multi-lingual colleagues is crucial to target any RaaS affiliate. And they really do go after anyone, they say – any group of interest to their customers and that the industry needs to understand more deeply is a target for the team's infiltrators. Thanks to extensive preparation and an experienced team, in most cases, they're successful on the first attempt. Long may it continue.
Billions of people around the world are expected to go to the polls in 2024 in what will be the most consequential election year in recent memory. Although many in the U.S. will be focused on what is expected to be a messy presidential contest at home, voters in the European Union, India, Russia and dozens of other countries will cast their ballots in parliamentary races, constitutional referendums, and presidential elections. Cybersecurity researchers and government officials are already warning that countries are cooking up influence operations in an effort to sway voters. Disinformation operations and hacking attempts on election infrastructure could also threaten to sow discord and undermine confidence in elections. Although the U.S. intelligence community said this week that they had no evidence that the 2022 midterm elections were targeted by a “whole-of-government influence campaign” like the one seen in 2016, they declared that Russia and China attempted to influence voters in more subtle ways. Researchers from Recorded Future, the publisher of The Record, also wrote last week that China, Russia, Iran, domestic violent extremists, and hacktivist groups will likely take advantage of the evolving geopolitical threat landscape — namely Russia’s war against Ukraine, Israel’s ongoing conflict with Hamas, and China’s increasing assertiveness over Taiwan — to aggressively target the U.S. election. “While advanced influence actors will very likely conduct pre-planned strategic influence operations, they will very likely opportunistically leverage official announcements, events, and public statements by prominent U.S. political figures, media personalities, celebrities, and U.S.-based organizations operating at the nexus of controversial political topics in tactical influence operations in pursuit of their objectives,” the report said. Some officials and social media executives have warned that it could be even more challenging to secure elections in 2024 than it was in 2016. Michigan Secretary of State Jocelyn Benson, for example, said last month that artificial intelligence can make it easier for threat actors to disseminate disinformation on a scale never seen before.
 web.archive.org
web.archive.org
Europol joined law enforcement agencies from 17 countries in warning 443 online sellers that the payment card data of their customers had been compromised. In a press release on Friday, the agency said the two-month operation was led by Greece and supported by cybersecurity firms Group-IB and Sansec — two companies with experience monitoring digital skimming attacks. In skimming attacks hackers embed tools or malware onto e-commerce sites that allow them to siphon credit card information from online stores during the checkout process. The tactic has long been a problem for popular internet sellers. With the help of several incident response teams and the European Union Agency for Cybersecurity (ENISA), hundreds of unnamed websites were notified that they were being used by hackers for digital skimming attacks. “Digital skimming attacks can go undetected for a long time. Payment or credit card information stolen as a result of these criminal acts is often offered for sale on illicit marketplaces on the darknet,” Europol said. “Customers are usually not aware that their payment details have been compromised until the criminals have already used them to carry out an unauthorized transaction. Generally, it is difficult for customers to find the point of compromise.” All of the law enforcement agencies worked with the online stores, providing technical assistance to help them remove the tools and protect customers. The countries involved in the effort included the United States, United Kingdom, Germany, Colombia, Spain, the Netherlands and more. The payment fraud industry has shown signs of recovery following Russian law enforcement's crackdown on domestic cybercriminals and the Russian invasion of Ukraine in 2022, according to an annual payment fraud report from Recorded Future, which owns The Record. Researchers found 119 million cards posted for sale on dark web carding shops, with an estimated $9.4 billion in preventable fraud losses for card issuers and $35 billion in potential chargeback fees for merchants and acquirers in 2023. In 2022, e-skimmers led to 45.6 million compromised payment card records posted for sale on dark web platforms, according to last year's report. The type of stores embedded with e-skimmers in 2023 included restaurants — which accounted for 18.5% of all victim companies — automotive parts sellers, clothing stores, and more. The U.S. had the most cards available with more than 50 million on the dark web. No other region or country tracked had more than 2.5 million. “Looking ahead to 2024, fraudsters are expected to refine their tactics, continuing to compromise cards using both old and new methods. Stolen payment cards from North American and European financial institutions led in volume throughout 2023 and are likely to persist in 2024. “The report concludes that in 2024, fraudsters will likely combine sophisticated technical solutions, nuanced workflows, and social engineering tactics to bypass rules-based fraud detection.”
 www.theregister.com
www.theregister.com
Cryptocurrency wallet maker Ledger says someone slipped malicious code into one of its JavaScript libraries to steal more than half a million dollars from victims. The library in question is Connect Kit, which allows DApps – decentralized software applications – to connect to and use people's Ledger hardware wallets. Pascal Gauthier, CEO of Ledger, in a public post said a former employee had been duped by a phishing attack, which allowed an unauthorized party to upload a malicious file to the company's NPM registry account. "The attacker published a malicious version of the [Ledger Connect Kit](https://www.npmjs.com/package/@ledgerhq/connect-kit?activeTab=versions) (affecting versions 1.1.5, 1.1.6, and 1.1.7)," said Gauthier. "The malicious code used a rogue WalletConnect project to reroute funds to a hacker wallet." The [malicious file](https://cdn.jsdelivr.net/npm/2e6d5f64604be31/2e6d5f64604be31.js) was what's known as a "[crypto drainer](https://blog.confiant.com/how-one-crypto-drainer-template-facilitates-tens-of-millions-of-dollars-in-theft-66f3794aea4b)" – it siphons funds from digital wallets. And because [dozens of crypto projects](https://sourcegraph.com/search?q=context:global+@ledgerhq/connect-kit&patternType=standard&sm=1&groupBy=repo) utilize the Connect Kit library, the potential financial loss could have been considerable. The damage however was limited because the compromised file was only live for about five hours and active for about two. During this period, it's [claimed](https://nitter.net/zachxbt/status/1735292040986886648) that the attacker managed to obtain more than $610,000 worth of crypto tokens. Revoke.cash, a service for revoking certain crypto transactions – which was affected by the incident – reports losses on the order of [$850,000](https://revoke.cash/exploits/ledger-connect-kit?chainId=1). According to Gauthier, the attack was addressed within 40 minutes of discovery, the attacker's blockchain address has been identified, and Tether has frozen the attacker's Tether tokens. Authorities, he claims, have been notified. "The authentic and verified version of the Ledger Connect Kit, version 1.1.8, is now in circulation and safe to use," said Gauthier. "Safe" may be overstating the case: According to security firm Socket, which provides algorithmic assessments of NPM packages, Connect Kit currently rates 51 out of 100 for Supply Chain Security and 55 out of 100 for Quality. Gauthier insists standard practice at Ledger is that no one person can deploy code without a multiparty review. "We have strong access controls, internal reviews, and multi-signature code when it comes to most parts of our development," he said. "This is the case in 99 percent of our internal systems. Any employee who leaves the company has their access revoked from every Ledger system." And yet Ledger's account of the incident – a former employee surrendered credentials to a phishing scheme, allowing a miscreant to gain access to Ledger's NPM account to push through bad code – suggests this was one occasion where company security controls fell short. According to Rosco Kalis, a software engineer for Revoke.cash, Ledger did not have two-factor authentication in place for NPM, which presumably would have prevented the phishing attack from working. What's more, Kalis [claimed](https://revoke.cash/blog/2023/ledger-connect-kit-hack-retrospective) Ledger failed to revoke code publication rights for its former employee. Gauthier characterized this fiasco as an "unfortunate isolated incident" and said, "Ledger will implement stronger security controls, connecting our build pipeline that implements strict software supply chain security to the NPM distribution channel." The Ledger leader's reference to the NPM distribution channel glosses over the way in which Connect Kit actually gets distributed. Kalis pointed out that Ledger distributes Connect Kit through a content delivery network (CDN), which means that developers cannot pin the library – limit it to a specific version. Instead, applications that depend on the library always fetch the latest release, which becomes problematic when the latest release has been hijacked. "Generally speaking, developers protect against supply chain attacks by 'pinning' the versions of dependencies that they install," Kalis said. Kalis accepted some of the blame by acknowledging that while Ledger should not have published its library in a way that did not support dependency pinning, Revoke.cash should have realized Connect Kit's distribution method posed a security risk. However, Kalis isn't ready to shoulder the burden of compensating those who have lost funds. "Due to the widespread nature of the exploit, it is impossible to determine which of the victims of the exploit got compromised on Revoke.cash and which got compromised on other websites," he wrote. "This is why we unfortunately do not see it as a feasible solution for Revoke.cash or other affected websites to directly compensate impacted users." Kalis says the only answer as he sees it is for victims to seek reimbursement for losses from Ledger, adding, "It is currently unclear if Ledger plans to do this." Ledger, based in France, did not immediately respond to a request for comment.
 www.theregister.com
www.theregister.com
Mortgage lender Mr Cooper has now admitted almost 14.7 million people's private information, including addresses and bank account numbers, were stolen in an earlier IT security breach, which is expected to cost the business at least $25 million to clean up. The financial firm [disclosed](https://www.theregister.com/2023/11/06/security_in_brief/) a network intrusion in October, and initially said the "isolated" incident "did not affect any of the company's clients' or partners' systems or technology." In notifications filed with the US states of California and Maine on Friday, the mortgage giant revealed that scope of the cyberattack was much worse than it believed: highly personal records belonging to millions were snatched by one or more miscreants. "Through our investigation, we determined that there was unauthorized access to certain of our systems between October 30, 2023 and November 1, 2023," according to a notice [[PDF]](https://regmedia.co.uk/2023/12/18/mr_cooper_data_breach_notification.pdf) sent to 14,690,284 people. "During this period, we identified that files containing personal information were obtained by an unauthorized party." This personal information included people's names, addresses, phone numbers, Social Security numbers, dates of birth, and bank account numbers. Those affected include anyone whose mortgage may have been previously acquired or serviced by Mr Cooper, Nationstar Mortgage LLC, Centex Home Equity, or another sister brand or servicing partner. Anyone who previously applied for a home loan with any of these lenders may also be affected, we're told. Mr Cooper was formerly known as Nationstar, and is based in Texas. While the company says it has not seen any evidence that this data has been used for identity theft or fraud, Mr Cooper said it will continue to monitor the dark web for any evidence that the thieves are sharing, leaking, or otherwise misusing the stolen files. Plus: All affected individuals will receive 24 months of free credit monitoring. When asked about the breach, a Mr Cooper spokesperson referred The Register to a [statement](https://www.mrcoopergroup.com/press-releases/mr-cooper-group-update-on-recent-cyber-incident/) on the biz's website.
 www.theregister.com
www.theregister.com
Multiple sources are confirming the resurgence of Qakbot malware mere months after the FBI and other law enforcement agencies shuttered the Windows botnet. Microsoft Threat Intelligence reckons a new Qakbot phishing campaign is active as of December 11 but attack attempts are currently low in volume. The gang targets the hospitality sector, initially using phishing emails containing malicious PDF attachments that they've doctored to look like they come from the US Internal Revenue Service (IRS). When opened, the PDF presents the target with an error screen indicating a preview of the document isn't available, alongside a button to download the document from "AdobeCloud." Multiple sources are confirming the resurgence of Qakbot malware mere months after the FBI and other law enforcement agencies shuttered the Windows botnet. Microsoft Threat Intelligence reckons a new Qakbot phishing campaign is active as of December 11 but attack attempts are currently low in volume. The gang targets the hospitality sector, initially using phishing emails containing malicious PDF attachments that they've doctored to look like they come from the US Internal Revenue Service (IRS). When opened, the PDF presents the target with an error screen indicating a preview of the document isn't available, alongside a button to download the document from "AdobeCloud." Germán Fernández, security researcher at CronUp, [said](https://nitter.net/1ZRR4H/status/1735944522075386332) the same PDF template was used by Pikabot operators just days earlier – Windows malware that shares many similarities with Qakbot. Both are being associated with attacks from the group Proofpoint tracks as TA577. Clicking the button in the PDF led to the download and installation of Qakbot, which Microsoft said may have been an updated payload. The previously unseen version, 0x500, was generated on December 11, according to its analysis. The team at Zscaler ThreatLabz [confirmed](https://nitter.net/Threatlabz/status/1735863156738871470) that the payload was updated, and the new version has a 64-bit architecture, uses AES for network encryption, and sends POST requests to path /teorema505. Two researchers at Proofpoint, Tommy Madjar and Pim Trouerbach, also [confirmed](https://nitter.net/ffforward/status/1736075488140079489) they had spotted updated Qakbot activity, but the new features only amount to "[minor tweaks](https://nitter.net/Myrtus0x0/status/1735931232436003108)." They added that the new Qakbot activity goes back to November 28, roughly two weeks further than December 11 – the date Microsoft first spotted it.
 therecord.media
therecord.media
Cable TV and internet service provider Xfinity says a breach linked to a widespread vulnerability in Citrix technology exposed data of about nearly 36 million people in mid-October. The intrusion happened between October 16-19, after Citrix had announced the bug but before Xfinity patched its systems, the Philadelphia-based company said in a [notification filed](https://apps.web.maine.gov/online/aeviewer/ME/40/49e711c6-e27c-4340-867c-9a529ab3ca2c.shtml) Monday with Maine regulators. The vulnerability, known as “Citrix Bleed” and tracked by researchers as CVE-2023-4966, affects NetScaler ADC and NetScaler Gateway appliances used by companies to manage network traffic. Since Citrix announced the bug on October 10, it has prompted warnings from cybersecurity experts and the federal government about exploitation by malicious hackers. Cybercrime groups are suspected to have used it in attacks against the healthcare, aviation, banking and manufacturing sectors, among others. Xfinity — a division of Comcast Corp., which also runs entertainment company NBCUniversal — said it patched its systems on October 23 after Citrix issued additional guidance. The regulatory filing does not specify exactly when Xfinity discovered the breach. On November 16, after the company had notified law enforcement and conducted an investigation, Xfinity “determined that information was likely acquired,” the regulatory filing said. The information included “usernames and hashed passwords; for some customers, other information was also included, such as names, contact information, last four digits of social security numbers, dates of birth and/or secret questions and answers.” Xfinity said it is still analyzing the breach and is telling customers that it will “provide additional notices as appropriate.” The company is asking customers to reset their passwords and is urging them to add two-factor authentication to their accounts.
 therecord.media
therecord.media
An FBI search warrant [unsealed](https://www.justice.gov/media/1329536/dl?inline=&utm_medium=email&utm_source=govdelivery) PDF Tuesday in the Southern District of Florida revealed that the FBI had help from a “confidential human source” in penetrating the AlphV/Blackcat ransomware gang’s network. Targeted darknet websites used by the cybercriminals were [replaced by a splashpage](https://therecord.media/alphv-black-cat-ransomware-takedown-fbi) on Tuesday, announcing they had been seized as part of a coordinated international law enforcement action. In an announcement following the upload of the splashpage, the U.S. Department of Justice revealed that the FBI had developed a decryption tool for the ransomware that has been offered to more than 500 victims globally to allow them to restore their encrypted systems. The tool has saved “multiple victims from ransom demands totaling approximately $68 million,” according to the DoJ, which described AlphV/Blackcat as “the second most prolific ransomware-as-a-service variant in the world based on the hundreds of millions of dollars in ransoms paid by victims around the world.” Alongside encrypting victim’s computer networks, the criminals also exfiltrate data from the target networks and subsequently publish it online in a secondary extortion bid. In an unusual incident in November, the gang even reported [one of its victims](https://therecord.media/meridianlink-confirms-cyberattack-after-sec-threat) to a regulator to increase the pressure on the victim. Alongside the DoJ announcement, Lisa Monaco, the Deputy Attorney General, said: “In disrupting the Blackcat ransomware group, the Justice Department has once again hacked the hackers,” referencing the agency’s [takedown of the Hive ransomware gang](https://therecord.media/we-hacked-the-hackers-doj-fbi-take-down-hive-ransomware-after-spending-months-inside-gang-systems). “With a decryption tool provided by the FBI to hundreds of ransomware victims worldwide, businesses and schools were able to reopen, and health care and emergency services were able to come back online. We will continue to prioritize disruptions and place victims at the center of our strategy to dismantle the ecosystem fueling cybercrime,” Monaco added. The [unsealed warrant](https://www.justice.gov/media/1329536/dl?inline=&utm_medium=email&utm_source=govdelivery) (PDF) does not detail the full extent of the FBI investigation into the ransomware gang, but reveals that as part of it the agency brought in a confidential human source “who routinely provides reliable information related to ongoing cybercrime investigations.” The source was able to help by responding to a public advertisement the ransomware gang had posted for potential affiliates, and — after being interviewed by the criminals to determine their “technical proficiency with network intrusion” — was given access credentials for the Blackcat’s affiliate system using a unique .onion address. Law enforcement was subsequently able to access the affiliate panel itself, pursuant to a separate federal search warrant, where they investigated how the system operated. “Affiliates use the panel to manage each ransomware attack on a victim throughout the attack lifecycle, from ransomware deployment through payment and decryption of victim data,” the warrant explained. The search warrant does not make clear how, but says “law enforcement gained visibility into the Blackcat Ransomware Group’s network.” As a result, the FBI was also able to identify and collect 946 public/private key pairs that the ransomware group used to operate its various Tor sites, including affiliate panels, leak sites, and sites for victim communications. The search warrant, which was certified last week on December 11, allowed the FBI to use these key pairs to seize the “Blackcat-linked victim communications sites, leak sites, and panel sites” hosted on the Tor network. “These actions are not the culmination of our efforts, they are just the beginning,” said Acting Assistant Attorney General Nicole Argentieri of the DoJ’s criminal division. “Criminal actors should be aware that the announcement today is just one part of this ongoing effort. Going forward, we will continue our investigation and pursue those behind Blackcat until they are brought to justice.” AlphV/Blackcat “has targeted the computer networks of more than 1,000 victims and caused harm around the world since its inception, including networks that support U.S. critical infrastructure,” the DoJ announced. It has caused disruption to critical infrastructure in the U.S., “including government facilities, emergency services, defense industrial base companies, critical manufacturing, and healthcare and public health facilities – as well as other corporations, government entities, and schools,” said the DoJ. The department estimated the gang had caused hundreds of millions in losses globally when accounting for “ransom payments, destruction and theft of proprietary data, and costs associated with incident response.”
 www.theregister.com
www.theregister.com
Hacktivists reportedly disrupted services at about 70 percent of Iran's gas stations in a politically motivated cyberattack. Iran's oil minister Javad Owji [confirmed](https://fararu.com/fa/news/691956/%D9%88%DB%8C%D8%AF%D8%A6%D9%88-%D9%88%D8%B2%DB%8C%D8%B1-%D9%86%D9%81%D8%AA-%D8%A8%D9%87-%D9%BE%D9%85%D9%BE%E2%80%8C%D8%A8%D9%86%D8%B2%DB%8C%D9%86%E2%80%8C%D9%87%D8%A7-%D8%AD%D9%85%D9%84%D9%87-%D8%B3%D8%A7%DB%8C%D8%A8%D8%B1%DB%8C-%D8%B4%D8%AF) on Monday the IT systems of the nation's petrol stations had been attacked as Iranian media told of long queues at the pumps and traffic jams – particularly in Tehran - as folks tried and failed to fill up. A spokesperson for the country's gas stations told the Fars News Agency insisted there was [no fuel shortage](https://www.farsnews.ir/en/news/14020927000684/Iran%27s-Fel-Delivery-Sysem-Resmes-Wrk-Afer-Cyberaack), just an inability to pump that fuel. "A software problem with the fuel system has been confirmed in some stations across the country and experts are currently fixing the issue," Reza Navar [claimed](https://www.reuters.com/world/middle-east/software-problem-disrupts-iranian-gas-stations-fars-2023-12-18/). Meanwhile, a group called Gonjeshke Darande – or Predatory Sparrow – claimed responsibility for taking out the gas pumps. This comes during a period of high tension in the Middle East stemming from the Israel-Hamas conflict over Gaza. "This cyberattack comes in response to the aggression of the Islamic Republic and its proxies in the region," the crew [declared](https://t.me/GonjeshkeDarandeOfficial/3) in its Telegram channel. "A month ago we warned you that we're back and that we will impose cost for your provocations. This is just a taste of what we have in store." Iran has accused the gang, which has also carried out cyberattacks on Iranian railway systems and a steel plant, of having [ties to Israel](https://cyberlaw.ccdcoe.org/wiki/Predatory_Sparrow_operation_against_Iranian_steel_maker_(2022)). After the digital intrusion into the Iranian steel plant's network in July 2022, which also caused a serious fire, Itay Cohen, head of cyber research at Check Point Software, [told the BBC](https://www.bbc.com/news/technology-62072480) that "given their sophistication, and their high impact, we believe that the group is either operated, or sponsored by, a nation state" – contrary to the crew's claim to be simple hacktivists. Predatory Sparrow also [bragged](https://twitter.com/darandegonjeshk/status/1736648198570025414) about the Iran gas station shutdown on Twitter, and said as with their "previous operations, this cyberattack was conducted in a controlled manner while taking measures to limit potential damage to emergency services. "We delivered warnings to emergency services across the country before the operation began, and ensured a portion of the gas stations across the country were left unharmed for the same reason, despite our access and capability to completely disrupt their operation."
 www.theregister.com
www.theregister.com
Cybercrime gangs like the notorious Lazarus group and spyware vendors like Israel's NSO should be considered cyber mercenaries – and become the subject of a concerted international response – according to a Monday report from Delhi-based think tank Observer Research Foundation (ORF). Author Fitri Bintang Timur [argued](https://www.orfonline.org/research/cyber-mercenaries) the term mercenary applies because, as amendments to the Geneva Convention put it, mercenaries are "an entity having the motivation to gain financial or material compensation in return for their willingness to fight for the recruiter's country." The modern equivalent is those who carry out their operations using information technology and networks – hence the term cyber mercenaries. Such groups have been noted and studied by groups like Citizen Lab and Amnesty International since the early 2010s but are often considered mere criminals. Timur argued that Lazarus Group earned the dubious title of cyber mercenary by working to develop and distribute malware on behalf of the North Korean government. She asserted that NSO Group joined the club by peddling its Pegasus spyware to governments willing to purchase and deploy it despite being a legitimate (if controversial) business. Other cyber mercenary operations offer hackers-for-hire. The report asserted that the market for cyber mercenaries is growing, as it is useful for state actors to improve their offensive capabilities while maintaining "plausible deniability through the avoidance of identification." Cyber mercenaries are also seen as cost effective. They don't require a human resource department, training, or other personnel costs. Nations that can’t afford an offensive cyber-ops crew may therefore hire cyber mercenaries to get into the game. While some work has been done to curb such actors, Timur suggested more needs to done. She called for legislation that aligns the use of intelligence and digital forensic tools with human rights obligations. She also states that standards must be set so that acts conducted in the name of national security also respect human rights declarations. Timur noted in her report that peaceful countries use legislative loopholes to "harbor cyber-mercenary subsidiaries and research centers" – an action that can turn sour, for instance when information is leaked or otherwise used for questionable purposes. For example, in the case of NSO Group, the EU Commission chose not to interfere with individual member states' use of its notorious Pegasus malware as it was categorized as a "national security" tool. Yet the software was used to target government officials, journalists, business people, activists, academics, and other targets that posed little plausible threat to safety – but may have been irritants to politicians. The report concludes by calling for citizens to demand accountability from governments and businesses who engage cyber mercenaries. Timur noted that civil society groups have taken action through lawsuits to demand better transparency.
 web.archive.org
web.archive.org
#### A hacker group calling itself Solntsepek—previously linked to Russia’s notorious Sandworm hackers—says it carried out a disruptive breach of Kyivstar, a major Ukrainian mobile and internet provider. Over nearly a decade, the hacker group within Russia's GRU military intelligence agency known as Sandworm has [launched some of the most disruptive cyberattacks in history](https://web.archive.org/web/20231213205125/https://www.wired.com/story/sandworm-kremlin-most-dangerous-hackers/) against Ukraine's power grids, financial system, media, and government agencies. Signs now point to that same usual suspect being responsible for sabotaging a major mobile provider for the country, cutting off communications for millions and even temporarily sabotaging the air raid warning system in the capital of Kyiv. On Tuesday, a cyberattack hit [Kyivstar](https://web.archive.org/web/20231213205125/https://www.wired.com/story/mariupol-ukraine-war/), one of Ukraine's largest mobile and internet providers. The details of how that attack was carried out remain far from clear. But it “resulted in essential services of the company’s technology network being blocked,” according to a [statement](https://web.archive.org/web/20231213205125/https://cip.gov.ua/en/news/fakhivci-cert-ua-doslidzhuyut-kiberataku-na-merezhu-telekom-operatora-kiyivstar) posted by Ukraine’s Computer Emergency Response Team, or CERT-UA. Kyivstar's CEO, Oleksandr Komarov, told Ukrainian national television on Tuesday, [according to Reuters](https://web.archive.org/web/20231213205125/https://www.reuters.com/technology/cybersecurity/ukraines-biggest-mobile-operator-suffers-massive-hacker-attack-statement-2023-12-12/), that the hacking incident “significantly damaged [Kyivstar's] infrastructure [and] limited access.” “We could not counter it at the virtual level, so we shut down Kyivstar physically to limit the enemy's access,” he continued. “War is also happening in cyberspace. Unfortunately, we have been hit as a result of this war.” The Ukrainian government hasn't yet publicly attributed the cyberattack to any known hacker group—nor have any cybersecurity companies or researchers. But on Tuesday, a Ukrainian official within its SSSCIP computer security agency, which oversees CERT-UA, pointed out in a message to reporters that a group known as Solntsepek had claimed credit for the attack in a Telegram post, and noted that the group has been linked to the notorious Sandworm unit of Russia's GRU. “We, the Solntsepek hackers, take full responsibility for the cyber attack on Kyivstar. We destroyed 10 computers, more than 4 thousand servers, all cloud storage and backup systems,” reads the message in Russian, addressed to Ukrainian president Volodymyr Zelenskyy and posted to the group's Telegram account. The message also includes screenshots that appear to show access to Kyivstar's network, though this could not be verified. “We attacked Kyivstar because the company provides communications to the Ukrainian Armed Forces, as well as government agencies and law enforcement agencies of Ukraine. The rest of the offices helping the Armed Forces of Ukraine, get ready!” Solntsepek has previously been used as a front for the hacker group Sandworm, the Moscow-based Unit 74455 of Russia's GRU, says John Hultquist, the head of threat intelligence at Google-owned cybersecurity firm Mandiant and a longtime tracker of the group. He declined, however, to say which of Solntsepek’s network intrusions have been linked to Sandworm in the past, suggesting that some of those intrusions may not yet be public. “It's a group that has claimed credit for incidents we know were carried out by Sandworm,” Hultquist says, adding that Solntsepek's Telegram post bolsters his previous suspicions that Sandworm was responsible. "Given their consistent focus on this type of activity, it's hard to be surprised that another major disruption is linked to them.” If Solntsepek is a front for Sandworm, it would be far from the first. Over its years of targeting Ukrainian infrastructure, the GRU unit has used a [wide variety of covers](https://web.archive.org/web/20231213205125/https://www.wired.com/story/russian-hackers-false-flags-iran-fancy-bear/), hiding behind false flags such as independent hacktivist groups and cybercriminal ransomware gangs. It even attempted to frame North Korea for its [attack on the 2018 Winter Olympics](https://web.archive.org/web/20231213205125/https://www.wired.com/story/untold-story-2018-olympics-destroyer-cyberattack/). Today, Kyivstar countered some of Solntsepek's claims in a post on X, writing that “we assure you that the rumors about the destruction of our ‘computers and servers’ are simply fake.” The company had also written on the platform that it hoped to restore its network's operations by Wednesday, adding that it's working with the Ukrainian government and law enforcement agencies to investigate the attack. Kyivstar's parent company, Veon, headquartered in Amsterdam, didn't respond to WIRED's request for more information. While the fog of war continues to obscure the exact scale of the Kyivstar incident, it already appears to be one of the most disruptive cyberattacks to have hit Ukraine since Russia's full-scale invasion began in February 2022. In the year that followed, Russia launched [more data-destroying wiper attacks](https://web.archive.org/web/20231213205125/https://www.wired.com/story/ukraine-russia-wiper-malware/) on Ukrainian networks than have been seen anywhere else in the world in the history of computing, though most have had far smaller effects than the Kyivstar intrusion. Other major Russian cyberattacks to hit Ukraine over the past 20 months include a cyberattack that crippled [thousands of Viasat satellite modems](https://web.archive.org/web/20231213205125/https://www.wired.com/story/viasat-internet-hack-ukraine-russia/) across the country and other parts of Europe, now believed to have been carried out by the GRU. Another incident of cybersabotage, which Mandiant attributes to Sandworm specifically, [caused a blackout in a Ukrainian city](https://web.archive.org/web/20231213205125/https://www.wired.com/story/sandworm-ukraine-third-blackout-cyberattack/) just as it was being hit by missile strikes, potentially hampering defensive efforts. It's not yet clear if the Kyivstar attack—if it was indeed carried out by a Russian state-sponsored hacker group—was merely intended to sow chaos and confusion among the company's customers, or if it had a more specific tactical intention, such as disguising intelligence-gathering within Kyivstar's network, hampering Ukrainian military communications, or silencing its alerts to civilians about air raids. “Telecoms offer intelligence opportunities, but they're also very effective targets for disruption," says Mandiant's Hultquist. “You can cause significant disruption to people's lives. And you can even have military impacts.”
 therecord.media
therecord.media
Dozens of cybersecurity experts and human rights groups have criticized the latest draft of the controversial UN Cybercrime Treaty currently being negotiated by member states, with some saying that it is significantly worse than the first draft. Several experts involved in the negotiating process told Recorded Future News that the [draft published](https://www.unodc.org/documents/Cybercrime/AdHocCommittee/Concluding_session/Documents/A_AC.291_22_Rev.1_E.pdf) late last month would effectively criminalize cybersecurity research and overlook human rights. “The latest UN cybercrime treaty draft not only disregards but also worsens our concerns. It perilously broadens its scope beyond the cybercrimes specifically defined in the Convention, encompassing a long list of non-cybercrimes,” said Katitza Rodriguez, policy director for global privacy at the Electronic Frontier Foundation (EFF). “This draft retains the concerning issue of expanding the scope of evidence collection and sharing across borders for any serious crime, including those crimes that blatantly violate human rights law. Furthermore, this new version overreaches in investigating and prosecuting crimes beyond those detailed in the treaty.” The treaty draft was prompted by a UN General Assembly vote in December 2019 to begin negotiating a cybersecurity accord after Russia took issue with the previous agreement — the [Budapest Convention](https://www.coe.int/en/web/cybercrime/the-budapest-convention) — and demanded something new to address the issue. After seeing the [first draft](https://therecord.media/un-cybercrime-treaty-negotiations-new-york) in August, human rights groups and even tech industry giants [like Microsoft](https://therecord.media/microsoft-opposes-draft-cybercrime-treaty) warned that significant changes need to be made to stop the treaty from being [used by governments as a tool of repression](https://therecord.media/global-cybercrime-treaty-disastrous-rights-orgs). An updated draft was published on November 28, following lengthy negotiating sessions. #### ‘Blatant disregard of our input’ Rodriguez said the initial draft of the treaty limited its scope to a detailed list of crimes involving technology. Rodriguez added that EFF is “deeply troubled by the blatant disregard of our input” which “moves the text further away from consensus.” “This isn't just an oversight; it's a significant step in the wrong direction,” she explained, noting that the original treaty was aimed at combating cybercrime but has since “morphed into an expansive surveillance treaty, raising the risk of overreach in both national and international investigations.” The new draft retains a controversial provision allowing states to compel engineers or employees to undermine security measures, posting a threat to encryption, according to Rodriguez. It also empowers states to cast a wider net by accessing data stored by companies abroad, potentially in violation of other nations’ privacy laws. “This new text not only falls short of reining in its intrusive surveillance powers but also endangers human rights, global cooperation, and cybersecurity; thereby undermining its original cybercrime-fighting intent,” she said in an email. Human Rights Watch acting associate director Deborah Brown said the latest draft is “primed to facilitate abuses on a global scale” because it gives governments expansive cross-border powers to investigate “virtually any imaginable crime – like peaceful dissent or expression of sexual orientation – while undermining the treaty’s purpose of addressing genuine cybercrime.” “Governments should not rush to conclude this treaty without ensuring that it elevates, rather than sacrifices, our fundamental rights,” she said. Governments will hold further negotiating sessions on December 19 and 20 in Vienna before the draft is [considered](https://www.unodc.org/unodc/en/cybercrime/ad_hoc_committee/ahc_concluding_session/main) in New York at the end of January. The treaty will be voted on by the full assembly during that January session. Since the initial draft was published, member states have battled over issues both big and small — including even basic topics like the definition of “cybercrime.” Many states, led by Russia and China, want an expansive treaty that would leave room for countries to effectively make their own localized determinations on what cybercrime is. The United States, European Union, several Latin American states and others are arguing for a more targeted treaty focused on core cybercrime offenses, as well as expanded surveillance and law enforcement cooperation between countries. Human rights activists and cybersecurity experts have been alarmed by stances taken on both sides, expressing concern about how the treaty will be abused by dictatorships as well as countries like the U.S. that are seeking to expand its surveillance capabilities on a global scale. A U.S. State Department spokesperson told Recorded Future News that the treaty is still under negotiation and they are preparing for the upcoming seventh round of negotiations. The spokesperson said they have “worked closely with U.S. stakeholders in this process and welcome their contributions.” “We look forward to working with Member States to finalize the treaty during the next session scheduled for January 29 to February 9, 2024 in New York,” the spokesperson said. #### Tech industry backlash Human rights groups aren’t the only ones criticizing the treaty — the tech industry has lodged similar complaints about the treaty’s lack of protections for cybersecurity researchers. The Cybersecurity Tech Accord — a global industry group [representing](https://cybertechaccord.org/signatories/) more than 157 large tech companies including Microsoft, Meta, Oracle, Cisco, SalesForce, Dell, GitHub, HP and more — published a warning this week saying it is “gravely concerned” by the direction of the UN cybercrime treaty negotiations and called for “extensive changes over the final draft text.” The Cybersecurity Tech Accord has been participating in the cybercrime treaty negotiating process since it began in 2021. The group warned that if adopted in its current form, the treaty would “erode data privacy, weaken cybersecurity, and undermine online rights and freedoms across the world.” The latest draft, they said, added concerning new provisions that cover any crime involving the use of technology, extend extraterritorial surveillance without safeguards, and allow legitimate cybersecurity research and penetration testing to be criminalized. “Without significant changes, this Convention will facilitate, rather than reduce, crime online,” said Nick Ashton-Hart, the Tech Accord’s head of delegation to the negotiations. “Among its many flaws are that it allows legitimate cybersecurity research and penetration testing to be criminalized. These activities are fundamental to securing online systems from criminal abuse. Creating legal hazard for these professionals will make systems globally more vulnerable to cybercrime, exactly the opposite of the Convention’s stated purpose.” The organization noted that it previously raised its concerns with the negotiating parties, providing comments and text suggestions to nations. But the latest draft did nothing to address them. Their main concerns include: - The removal of sections that limit the treaty’s powers to narrowly-defined cybercrimes - Nation-state surveillance across borders without safeguards - Now-optional protections for cybercrime victims - Expansion of the “online fraud” concept Ashton-Hart added that any UN member state should be concerned about creating a convention “that allows every government in the world to transfer the personal information of citizens between themselves in secret in perpetuity, and to force the service providers who are responsible for that data to hand it over without any ability to object or refuse on any grounds.” He expressed particular disappointment with democratic states, virtually all of which “have not objected to this glaring lack of transparency and due process given it isn’t congruent with their own legal systems – or with democratic values.” Dev Stahlkopf, chief legal officer at Cisco, said that while international alignment on the investigation and prosecution of cybercrime is needed, respecting privacy and human rights is paramount. The group said the treaty needs to be narrowed to focus only on cyber-dependent crimes, limit the definition of cybercrime to stop the potential for states to use the treaty as a means of repression, limit government access to personal data, add in robust human rights safeguards and provide exemptions for cybersecurity researchers. #### Backsliding Raman Jit Singh Chima, senior international counsel for Access Now, told Recorded Future News that the latest draft walks back some of the discussions that were had in New York in August. In many ways, the latest draft reopens areas that human rights experts thought had been shut down based on discussions with negotiating parties. Many potential additions related to human rights, safeguards and procedural checks were not included in the new version. It appears, he said, that the treaty was negotiated down conservatively in order to accommodate the concerns of some negotiating states who “seem to be averse to civil society being specifically mentioned in the treaty.” “What's particularly concerning from our perspective is that this treaty does not address the concerns relating to providing strong safeguards and clarifying that the work of security researchers as well as the legitimate security research that might be conducted by journalists, civil society and others, should not be included in the scope of criminalization,” he said. Negotiating states have not learned from the [mistakes](https://therecord.media/cfaa-change-doj-good-faith-cybersecurity-research) seen with the Computer Fraud and Abuse Act in the U.S. and other laws that have been used to charge and imprison cybersecurity researchers, he said. Singh Chima added that any laws based on the treaty would create legal uncertainty and “a potential chilling effect” to legitimate security research. Based on the current draft, he said it is unclear whether it has a chance of advancing considering how little time is left for negotiators. “It's quite unclear at this point of time whether there will be full consensus achieved in the January-February session. Negotiating states would barely have a few weeks after [the December 18th session] to further improve the text for substantive negotiations, so right now, the odds are stacked against this treaty reaching consensus,” he said.
 therecord.media
therecord.media
The Federal Communications Commission is warning mobile phone service providers to ensure they are shielding customers from cybercriminals who use fraudulent SIM swaps to take over unwitting victims’ mobile phone accounts. The warning comes on the heels of a [Cyber Safety Review Board (CSRB)](https://therecord.media/sim-swapping-lapsus-cyber-safety-review-board-report) finding announced in August. The board detailed the operations of the hacking group [Lapsus$](https://therecord.media/tag/lapsus$), which was known for using SIM swaps to extort victims worldwide. The [new advisory](https://www.fcc.gov/document/fcc-reminds-carriers-prevent-sim-fraud-schemes), issued Monday by the FCC’s Privacy and Data Protection Task Force, says SIM swap fraud is increasing. It includes a reminder of updated requirements for telecommunications service providers to better guard consumer data. SIM swappers seek to dupe mobile carriers into transferring a victim’s phone number to a new device, which is then used for fraudulent activity. Scammers have figured out how to take advantage of lax multifactor authentication practices, according to the CSRB, which urged mobile operators to move away from using easily intercepted methods like text-message codes. The updated FCC rules mandate that carriers do more to securely verify customers identities prior to linking phone numbers to new devices or carriers. “Cell phone service providers are high-value targets for cybercriminals and scammers because in many instances they serve as the primary means consumers use today to access their most important and valuable financial and personal information,” Loyaan Egal, FCC Enforcement Bureau Chief and chair of the Privacy and Data Protection Task Force, said in a press release. The agency said carriers must quickly alert customers of account changes including whenever a password, customer response to “a carrier-designed back-up means of authentication,” or other records are altered. While not a SIM swap, an incident last week in which Verizon gave a woman’s stalker access to her data — including her address and phone records — underscored the dangers of carriers failing to protect customers. The incident, which was first reported by 404 Media in conjunction with Court Watch, revealed that the stalker used a blatantly fake search warrant to obtain the records from the carrier.
 therecord.media
therecord.media
Ukraine's defense intelligence directorate (GUR) said it infected thousands of servers belonging to Russia's state tax service with malware, and destroyed databases and backups. During the operation, Ukraine's military spies said they managed to break into one of the "key well-protected central servers" of Russia's federal tax service (FNS) as well as more than 2,300 regional servers throughout Russia and occupied Crimea. The attack also affected a Russian tech company that operates FNS’s database. According to GUR’s [statement](https://gur.gov.ua/content/zlam-federalnoi-podatkovoi-sluzhby-rf-detali-cherhovoi-kiberspetsoperatsii-hur.html) published Tuesday, the attack led to the “complete destruction” of the agency’s infrastructure. GUR claimed they destroyed configuration files "which for years ensured the functioning of Russia's tax system." Internet connection between FNS’ central office in Moscow and thousands of its regional branches is also “paralyzed,” GUR said. According to Ukraine’s intelligence, the FNS "has been unsuccessfully trying to restore the work of its service for four days in a row," but it will probably remain "paralyzed" for at least a month and "will never fully recover from the attack." The claims have not been independently verified — Russian state media has kept silent about the hack, and FNS hasn’t publicly reacted to it. It’s the second operation on a Russian state agency that GUR has taken responsibility for. In November, the agency [acknowledged](https://therecord.media/ukraine-cyber-operation-russian-aviation-agency) that it was behind "a successful cyber operation" against the Russian government's civil aviation agency, also known as Rosaviatsia. Until recently, only pro-Ukraine hacker groups and hacktivists have publicly claimed such attacks, including those targeting Russian airlines, banks, and internet providers. In October, a source within Ukraine's security services (SBU) told Recorded Future News that the agency collaborated with pro-Ukrainian hackers to breach Russia's largest private bank. In November, Ukrainian media [reported](https://www.pravda.com.ua/news/2023/11/29/7430924/) that the Ukrainian hacker group Blackjack worked with the SBU to hack into the website of Russia's Labor Ministry. They allegedly managed to obtain personal data of military personnel and information concerning Russia’s military actions in Ukraine. The SBU has not publicly acknowledged the incident.
 reclaimthenet.org
reclaimthenet.org
The video hosting platform Rumble, known for advocating free speech, just experienced a severe cyber attack. This incident occurred not long after the platform began hosting new security camera footage from the events of January 6th 2021, and Rumble’s CEO makes a direct correlation between the two events. As we reported last week, the Republican-led Subcommittee on Oversight of the Committee on House Administration last week unveiled their new Rumble channel. This channel was dedicated to publishing hours of footage from the Capitol Police.  Soon after the footage was uploaded, Rumble suffered a significant, coordinated cyber attack. This disruption made it impossible for users to upload or view any content on the platform. Rumble’s CEO, Chris Pavlovski, addressed the situation on X, stating, “I can confirm that this attack has been unprecedented and has been happening since this weekend.” Pavlovski also expressed his suspicion that the attack was politically motivated, likely perpetrated by activists or organizations opposed to the J6 videos on Rumble. The attack was remedied on Monday evening.  In a statement, the company expressed its gratitude, saying, “A major thank you to our cyber security partners and our entire team. This was a massive learning experience that will only make us stronger.” They also extended their appreciation to all users and creators for their patience during the disruption.
 therecord.media
therecord.media
Public-facing servers at a U.S. federal agency were compromised by hackers in June and July through a vulnerability in a popular product from Adobe, according to the nation’s leading cybersecurity agency. The unidentified hackers exploited CVE-2023-26360 — a bug affecting Adobe ColdFusion versions 2018 Update 15 (and earlier) and 2021 Update 5 (and earlier) as well as earlier installations of the software that Adobe no longer supports. ColdFusion is a tool used by organizations for rapid web-application development, allowing them to build web applications and integrate things like databases and other third-party libraries. An analysis of network logs confirmed the compromises, according to the Cybersecurity and Infrastructure Security Agency (CISA). “In June 2023, through the exploitation of CVE-2023-26360, threat actors were able to establish an initial foothold on two agency systems in two separate instances,” CISA [said in an advisory](https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-339a) on Tuesday. The advisory does not name the agency. CISA said it does not know if the same hackers perpetrated both attacks. “In both incidents, Microsoft Defender for Endpoint (MDE) alerted of the potential exploitation of an Adobe ColdFusion vulnerability on public-facing web servers in the agency’s pre-production environment,” CISA said. The affected agency was running outdated versions of software vulnerable to several bugs including CVE-2023-26360, the advisory said. CISA’s analysis showed the hackers inserted malware and were mainly launching a reconnaissance campaign. There is no evidence of data exfiltration or lateral movement by the hackers, CISA said. As early as June 2, the intruders exploited the vulnerability to gain access to a public-facing server, CISA said. The hackers tried to exfiltrate some files, but the attempt was not successful because the activity was detected and “quarantined,” the advisory said. Other attempts to download data were blocked by the victimized server. The hackers were able to view data contained in a ColdFusion file that contained the encryption method used to encrypt ColdFusion passwords, CISA said. Hackers again gained a foothold on June 26 after attacking a public-facing web server running ColdFusion, the advisory said. The agency removed the server from the network within 24 hours of receiving an alert. The malware used on the server during this incident attempted to decrypt passwords for ColdFusion data sources, but it only worked on ColdFusion version 8 or older. The version used by the agency was newer, CISA said. Spotted in the spring CISA noted that it [added CVE-2023-26360 to its list](https://www.cisa.gov/known-exploited-vulnerabilities-catalog?search_api_fulltext=CVE-2023-26360&sort_by=field_date_added&items_per_page=20) of Known Exploited Vulnerabilities in March and ordered all federal agencies to patch the flaw by April 5. Adobe has [warned](https://therecord.media/cisa-warnings-adobe-microsoft-citrix-vulnerabilities) throughout 2023 of [vulnerabilities](https://therecord.media/adobe-patches-dozens-of-vulnerabilities) affecting ColdFusion. In October, researchers at cybersecurity company Sophos said they saw hackers use a knockoff of the LockBit ransomware to target [outdated and unsupported Adobe ColdFusion servers](https://therecord.media/lockbit-knockoffs-proliferate-leaked-toolkit). CISA’s report highlights the necessity of federal agencies to use logging software as a way to identify security incidents. A report issued Monday from the U.S. Government Accountability Office [said](https://www.gao.gov/products/gao-24-105658) many civilian agencies “have not met the federal requirements for event logging — i.e., ensuring that cybersecurity incidents are tracked and that these tracking logs are appropriately retained and managed.” “Information from federal IT logs is invaluable in the detection, investigation, and remediation of cyberthreats,” they said. “We recommended that federal agencies fully implement requirements to log cybersecurity events, and more.” Twenty of 23 major civilian agencies examined “have not met requirements for investigation and remediation (event logging) capabilities.” The agencies were required to meet certain logging requirements by August. CISA did not specify in Tuesday’s advisory if the two attacked agencies were subject to that requirement. “Until the agencies implement all event logging requirements, the federal government's ability to fully detect, investigate, and remediate cyber threats will be constrained,” the GAO said. “Agencies described three key challenges that hindered their abilities to fully prepare to respond to cybersecurity incidents: (1) lack of staff, (2) event logging technical challenges, and (3) limitations in cyber threat information sharing.”
 therecord.media
therecord.media
Researchers have discovered more than 20 security flaws affecting routers manufactured by the Canadian communications equipment vendor Sierra Wireless. The company’s AirLink cellular routers are often used in critical infrastructure sectors, such as government and commercial facilities, emergency services, energy, transportation, water and healthcare. These routers connect critical local networks to the internet via cellular connections such as 3G and 4G. In a [report published](https://www.forescout.com/blog/sierra21-supply-chain-vulnerabilities-iot-ot-routers/) on Tuesday, California-based cybersecurity firm Forescout Vedere Labs said it found more than 86,000 of these routers exposed online. Most of them are used in the U.S., Canada, Australia, France, and Thailand. Among 21 new vulnerabilities discovered by researchers, one has a critical severity score and nine have a high severity score. Industries like manufacturing and healthcare are among the most affected, researchers said. In addition to routers, the researchers also found vulnerabilities in open-source components used in a variety of other products. For example, one critical flaw tracked as CVE-2023-41101 was found in OpenNDS — a service that separates the public local area network (LAN) from the internet. According to researchers, potential attackers could exploit the newly identified vulnerabilities to gain complete control over routers in critical infrastructure, allowing them to disrupt the network, spy on their victims, or deploy additional malware. For instance, in a healthcare facility, attackers could take control of a router to target devices belonging to patients, guests, or staff, thereby distributing further malware. Similarly, in the manufacturing industry, attackers could seize control of a router within a plant to launch attacks on industrial equipment. In addition to human attackers, these vulnerabilities can be exploited by botnets — groups of devices used by hackers to send spam emails, spread malware, or launch cyberattacks. Previous botnets, such as IoTroop/Reaper, [have targeted](https://usatcorp.com/airlink-bulletin-2-iotroop-reaper-malware/) exposed Sierra Wireless routers using default or stolen passwords and zero-day vulnerabilities The researchers didn't mention whether the vulnerabilities have been exploited in the wild. Sierra Wireless, which did not respond to requests for comment, has released an update to address the new vulnerabilities. The OpenNDS project has also already released an update that contains fixes for all reported vulnerabilities. Security flaws in routers and network infrastructure have been among the most exploited types of bugs recently, according to Forescout Vedere Labs. State-sponsored actors have been developing custom malware to use routers for espionage, while cybercriminals often use them to form botnets. In April of this year, for example, U.S. technology giant Cisco warned about attacks on routers allegedly being carried out by Russian military hackers to target victims in Europe, U.S. government institutions and approximately 250 Ukrainian victims.
 blog.talosintelligence.com
blog.talosintelligence.com
### Multiple vulnerabilities in Foxit PDF Reader Discovered by Kamlapati Choubey. Foxit PDF Reader contains multiple vulnerabilities that could lead to remote code execution if exploited correctly. [TALOS-2023-1837](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1837) (CVE-2023-32616) and [TALOS-2023-1839](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1839) (CVE-2023-38573) can be exploited if an attacker embeds malicious JavaScript into a PDF, and the targeted user opens that PDF in Foxit. These vulnerabilities can trigger the use of a previously freed object, which can lead to memory corruption and arbitrary code execution. [TALOS-2023-1838](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1838) (CVE-2023-41257) works in the same way, but in this case, it is caused by a type confusion vulnerability. Three other vulnerabilities could allow an attacker to create arbitrary HTA files in the context application, and eventually gain the ability to execute arbitrary code on the targeted machine. [TALOS-2023-1832](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1832) (CVE-2023-39542), [TALOS-2023-1833](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1833) (CVE-2023-40194) and [TALOS-2023-1834](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1834) (CVE-2023-35985) are all triggered if the targeted user opens a specially crafted file in the Foxit software or browser plugin. ### GPSd NTRIP Stream Parsing access violation vulnerability Discovered by Dimitrios Tatsis. An integer overflow vulnerability exists in the NTRIP Stream Parsing functionality of GPS daemon, which is used to collect and display GPS information in other software. A specially crafted network packet can lead to memory corruption. An attacker can send a malicious packet to trigger TALOS-[2023-1860](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1860) (CVE-2023-43628). [According to GPSd’s](https://gpsd.gitlab.io/gpsd/#support) website, this service daemon powers the map service on Android mobile devices and is “ubiquitous in drones, robot submarines, and driverless cars.” ### Buildroot - embedded Linux systems builder tool Discovered by Claudio Bozzato and Francesco Benvenuto. Talos researchers recently found multiple data integrity vulnerabilities in Buildroot, a tool that automates builds of Linux environments for embedded systems. An adversary could carry out a man-in-the-middle attack to exploit [TALOS-2023-1845](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1845) (CVE-2023-43608) and [TALOS-2023-1844](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1844) (CVE-2023-45842, CVE-2023-45839, CVE-2023-45838, CVE-2023-45840 and CVE-2023-45841) to execute arbitrary code in the builder. As a direct consequence, an attacker could then also tamper with any file generated for Buildroot’s targets and hosts. ### Malformed Excel file could lead to arbitrary code execution in WPS Office Discovered by Marcin “Icewall” Noga. An uninitialized pointer use vulnerability ([TALOS-2023-1748](https://talosintelligence.com/vulnerability_reports/TALOS-2023-1748)/CVE-2023-31275) exists in the functionality of WPS Office, a suite of software for word and data processing, that handles Data elements in an Excel file. A specially crafted malformed Excel file can lead to remote code execution. WPS Office, previously known as a Kingsoft Office, is a software suite for Microsoft Windows, macOS, Linux, iOS, Android, and HarmonyOS developed by Chinese software developer Kingsoft. It is installed by default on Amazon Fire tablet devices. Talos disclosed this vulnerability in November despite no official fix or patch from Kingsoft after the company did not respond to our notification attempts and failed the 90-day deadline as outlined in [Cisco’s third-party vendor vulnerability disclosure policy](https://sec.cloudapps.cisco.com/security/center/resources/vendor_vulnerability_policy.html).
 therecord.media
therecord.media
The Seoul Metropolitan Police on Tuesday accused a North Korean hacking group of targeting South Korean companies connected to the defense industry and stealing sensitive information about anti-aircraft weapon systems. In a press release publicizing the investigation into the Andariel hacking group — which has links to the notorious Lazarus Group — police said they seized servers in South Korea used by the group, conducted forensic searches of cellphones and laptops, and had searched the residence of a “foreign” woman accused of laundering the proceeds of ransomware attacks. The investigation was conducted alongside the FBI. Andariel is connected to North Korea’s intelligence office, the Reconnaissance General Bureau, which also houses Lazarus Group, according to government officials. The group was sanctioned in 2019 by the U.S. Treasury, which [said](https://home.treasury.gov/news/press-releases/sm774) the group “consistently executes cybercrime to generate revenue and targets South Korea’s government and infrastructure in order to collect information and to create disorder.” According to Seoul investigators, the hackers specifically targeted defense companies — stealing “technical data” on anti-aircraft systems — as well as research institutes and pharmaceutical companies. They determined that 1.2 terabytes of data had been stolen in attacks and notified the relevant companies, some of which were unaware they had been targeted. Others had contacted police when they discovered a breach, while in some cases “damage was not reported” to authorities. The hackers allegedly used a South Korean domestic server rental company as a “base for hacking,” with 83 connections made from a part of downtown Pyongyang where the International Telecommunications Bureau is housed. Investigators tracked paid ransoms on the cryptocurrency platforms Binance and Bithumb, including about $76,000 transferred into an account at a Chinese bank, where the funds were taken out at a branch close to the border with North Korea. Separately, investigators found the group extorted three ransomware victims in South Korea and abroad for about $357,000 worth of Bitcoin. Last month, the United Kingdom and South Korea issued a [joint advisory warning](https://therecord.media/south-korea-uk-warning-supply-chain-attacks-north-korea) of supply-chain attacks carried out by North Korean hackers. Also in November, the U.S., Japan and South Korea agreed to convene a consultative body on a quarterly basis for the purpose of “jointly preparing measures to block cyber activities that are abused as a major source of funds for North Korea's weapons development, such as nuclear weapons and WMD,” the South Korean government [said](https://www.president.go.kr/newsroom/press/KZfq8dqk).
 www.theregister.com
www.theregister.com
The bug that was very occasionally corrupting data on file copies in OpenZFS 2.2.0 has been identified and fixed, and there's a fix for the previous OpenZFS release too. The OpenZFS development team have put out not one but two new releases of the open-source cross-platform filesystem for Linux and FreeBSD. [Version 2.2.2](https://github.com/openzfs/zfs/releases/tag/zfs-2.2.2) fixes the problem that showed up in the latest version, which is included in FreeBSD 14 as well as several Linux distros, including Ubuntu 23.10. There's also a new release in the previous version of OpenZFS: [version 2.1.14](https://github.com/openzfs/zfs/releases/tag/zfs-2.1.14) which applies to FreeBSD back to version 12. This was necessary because while, as we [reported a week ago](https://www.theregister.com/2023/11/27/openzfs_2_2_0_data_corruption/), it was OpenZFS 2.2.0 that brought the issue to light and made it visible, it didn't actually cause the problem. It merely exposed an underlying bug which had been around for years: OpenZFS 2.2.0's new, faster copy function simply made the existing issue much more likely to happen. The FreeBSD project has [published an errata notice](https://www.freebsd.org/security/advisories/FreeBSD-EN-23:16.openzfs.asc), and made fixes available for FreeBSD 12, 13 and 14. The investigation that's been going on since then has revealed more. For instance, the bug was also confirmed in Illumos, the open-source fork of OpenSolaris which has continued development since [Oracle killed off the open source project in 2010](https://www.theregister.com/2010/08/13/opensolaris_is_dead/). Illumos is itself the basis of [several OpenSolaris-based](https://www.theregister.com/2022/12/07/new_version_of_openindiana/) distributions. As amendments in the release notes for both these versions clarify, it's also slightly worse than it looked last week, when we wrote that: >For Linux users, an additional condition seems to be that the OS has a recent version of the coreutils package – above version 9.x. This looked to be the case because the cp command in Coretils 9 was updated to look for ways to speed up file copies, such as checking for "holes" in files – long stretches of zeroes – called the [SEEK_HOLE optimization](https://lwn.net/Articles/440255/). Unfortunately, it looks like Red Hat backported this functionality from Coreutils 9.x to 8.x, and it's [been identified](https://github.com/openzfs/zfs/issues/15526#issuecomment-1835465225) in CentOS Stream 9 as well as in the [OpenELA source code](https://gitlab.com/redhat/centos-stream/rpms/coreutils/-/blob/c9s/coreutils-8.32-cp-file-range.patch?ref_type=heads). As the code comment dryly says: >I'd link to the corresponding RHEL code, but sadly they no longer publish it. RHEL doesn't include OpenZFS, so this data-loss issue will not affect it. Indeed, RHEL [doesn't even include Btrfs](https://www.theregister.com/2017/08/16/red_hat_banishes_btrfs_from_rhel/)… but [Oracle Linux does](https://www.theregister.com/2022/07/12/oracle_linux_9/), although that's no cause for concern here: Btrfs itself is immune from the bug. What this illustrates, though, is the problem with trying to pin down affected versions. As we [described back in June](https://www.theregister.com/2023/06/30/enterprise_distro_feature_devconf/), Red Hat puts a lot of engineering time and effort into backporting features from newer kernels into its very-long-term supported enterprise kernels. Sometimes, these backports may not be limited to the kernel: they may extend to non-kernel system utilities. These optimizations are perfectly safe on the Big Purple Hat's own distro, and indeed its RHELatives such as Oracle and Alma and so on. However, such changes can get picked up by other distros, or even by people hand-building complex bespoke installations. The result is that it's not safe to simply say "this only affects systems with coreutils 9 or above". At any rate, for now, the issue is fixed. There's a newer [overview of the issue](https://gist.github.com/rincebrain/e23b4a39aba3fadc04db18574d30dc73) on Github, but the investigation as to when the bug first appeared is still underway, as the comments there show (along with a link to our earlier story). The bug might go back as far as 2006. Although [bug fix #15571](https://github.com/openzfs/zfs/pull/15571) in these two new OpenZFS releases does resolve the issue, another, newer attempt to fix the issue in a cleaner way is also under investigation as [bug fix #15615](https://github.com/openzfs/zfs/pull/15615). ZFS is a complex filesystem, and this is a complex bug that may have remained hidden for 17 years. If there is a simpler, cleaner way to fix the issue, that would be a good thing.


