Sidebar
Cryptography
I have been thinking about implementing this for quite some time, but I would like some feedback from people more knowledgeable than me on the matter. There's been some great progress in the field of Private Information Retrieval (PIR) protocols. Recently, in a 2022 article, Lin et al. describe an "updateable DEPIR", with both read and write times that can be made sublinear to database size. I wonder if one couldn't use a combination of this technique and regular public-key cryptography to provide fully anonymous message routing. One could write outgoing messages to a fixed address and issue private reads to their contacts' addresses, with the messages themselves being encrypted with the receiver's public key. The benefit of this would be a messaging protocol wherein the server wouldn't just be oblivious to the content of all messages, but also the social graph itself, plus all message-sending operations becoming deniable as a side effect.
via https://cr.yp.to/talks.html#2022.11.10
In this six minute video, Robert Miles explains public/private key cryptography in layman's terms. As a non-expert in this field, I find Miles' explanation very accessible, and I've come back to this video to brush up on this concept several times since the first time I watched it. Enjoy!
[https://github.com/positive-intentions/chat](https://github.com/positive-intentions/chat) Is this a secure messaging app? probably not... but id like to share some details about how my app works so you can tell me what im missing. id like to have wording in my app to say something like "most secure chat app in the world"... i probably cant do that because it doesnt qualify... but i want to understand why? im not an expert on cyber security or cryptography. im sure there are many gaps in my knowlege in this domain. using javascript, i created a chat app. it is using peerjs-server to create an encrypted webrtc connection. this is then used to exchange additional encryption keys from cryptography functions built into browsers to add a redundent layer of encryption. the key exchange is done like diffie-helman over webrtc (which can be considered secure when exchanged over public channels). the algorithms are fairly easy to use and interchangable as described [here](https://developer.mozilla.org/en-US/docs/Web/API/SubtleCrypto/generateKey). * i sometimes recieve feedback like "javascript is inherently insecure". i disagree with this and have opened sourced my cryptography module. its basically a thin wrapper around vanilla crypto functions of a browser. [a prev post](https://www.reddit.com/r/cryptography/comments/1cint8h/what_are_your_thoughts_on_subtlecrypto_vs_wasm/) on the matter. * another concern for my kind of app (PWA) is that the developer may introduce malicious code. this is an important point for which i open sourced the project and give instructions for selfhosting. selhosting this app has some unique features. unlike many other selfhosted projects, this app can be hosted on github-pages for free (instructions are provided in the readme). im also working on introducing a way that users can selfhost federated modules. [a prev post](https://www.reddit.com/r/selfhosted/comments/1ecsst5/selfhosted_federated_modules/) on the matter. * to prevent things like browser extensions, the app uses strict CSP headers to prevent unauthorised code from running. selfhosting users should take note of this when setting up their own instance. * i received feedback the Signal/Simplex protocol is great, etc. id like to compare that opinion to the observation in how [my todo app ](https://p2p.positive-intentions.com/?path=/docs/demo-todo-list--docs) demo works. (the work is all experimental work-in-progress and far from finished). the demo shows a simple functionality for a basic decentralized todo list. this should already be reasonably secure. i could add handlers for exchanging keys diffie-helman style. which at this point is relatively trivial to implement. I think it's simplicity could be a security feature. * the key detail that makes this approach unique, is because as a webapp, unlike other solutions, users have a choice of using any device/os/browser. i think if i stick to the principle of avoiding using any kind of "required" service provider (myself included) and allowing the frontend and the backend to be hosted independently, im on track for creating a chat system with the "fewest moving parts". im hope you will agree this is true p2p and i hope i can use this as a step towards true privacy and security. security [might be further improved](https://www.reddit.com/r/WebRTC/comments/1e7sq0b/webrtc_ip_leaking_advice_wanted/) by using a trusted VPN. i created a[ threat-model](https://positive-intentions.com/docs/research/threat-model/) for the app in hopes that i could get a pro-bono security assessment, but understandable the project is too complicated for pro-bono work. i contacted "Trail of bits" because of their work on SimpleX and they have quoted me $50,000. the best i can offer is "open-source and communicating on reddit". (note: i asked them if i can share those details... summarized response: the SOW is confidential, but i can share the quote.) while there are several similar apps out there like mine. i think mine is distinctly a different approach. so its hard to find best practices for the functionalities i want to achieve. in particular security practices to use when using p2p technology. (note: this app is an unstable, experiment, proof of concept and not ready to replace any other app or service. It's far from finished and provided for testing and demo purposes only.) * Github: [positive-intentions/chat](https://github.com/positive-intentions/chat) * More information about the app: [positive-intentions.com](http://positive-intentions.com/) * Follow the subreddit: [r/positive\_intentions](https://www.reddit.com/r/positive_intentions/)
This is a technical but quite informative article, nominally about which elliptic curves have good security properties, but also discusses the intentions behind using EC instead of older systems like RSA (basically, EC is safer against some known classes of attacks). Posting partly because EC vs RSA came up here a few days ago.
cross-posted from: https://lemmy.world/post/18617290 > The National Institute of Standards and Technology has finally published the world’s first three official post-quantum cryptographic algorithms, tools designed to protect key systems against future quantum computers powerful enough to crack any code generated by a modern computer.

https://github.com/umutcamliyurt/TimeLockCrypt
 www.newscientist.com
www.newscientist.com
cross-posted from: https://sopuli.xyz/post/14485657 > In case of paywall: https://archive.is/kZAgI
 github.com
github.com
in my messaging app, javascript cryptography is the backbone of security so its important for it to be reliable. i would like to introduce you to my decentralized chat app: https://github.com/positive-intentions/chat i created thin wrapper around browser-based cryptography functions provided by the browser. it is using webpack 5 module federation to import it at runtime. https://github.com/positive-intentions/cryptography/blob/staging/src/stories/components/Cryptography.tsx with this i think i can effectively create encrypted p2p, which i hope to be a step towards true security (but it will take a while to get there). (note: my app is an experimental unstable proof-of-concept. it is provided for demo and testing purposes.)
So, I've had a bit of a stupid idea for my next programming project, which would be implementing a Microsoft Recall alternative for Linux where the data is encrypted. I've now written a bit of code and have come to the point where I'd need to encrypt the files. My plan was to use asymmetric encryption where the secret key is again encrypted using something like AES and the user needs to decrypt the private key to view the screenshots taken / data extracted from the screenshots. I have now learned that asymmetric encryption is very slow and it's generally not designed to encrypt large chunks of data, so I'm not sure how to continue. Do you think asymmetric encryption is feasible for this? Any idea how else to do the encryption? Ideally I would like for the server that takes the screenshots to not have a key that can decrypt the files since that wouldn't be as secure.
 blog.cryptographyengineering.com
blog.cryptographyengineering.com
writeup from the researcher who discovered this: https://www.openwall.com/lists/oss-security/2024/04/15/6

Hatching Secret Sauce Eggs is a Rooster's Business This is how I make the secret sauce. The recipe is inside the egg. [@cryptography@lemmy.ml](https://lemmy.ml/c/cryptography)
 blog.cryptographyengineering.com
blog.cryptographyengineering.com

Greetings !cryptography@lemmy.ml! At dyne, we're working relentlessly to democratize the power of computing. We've built an open source, multiplatform, tiny, secure, virtual machine for cryptography and blockchain interop. It's called Zenroom. Part of the philosophy behind it is to empower people who know what to do with data, not only the developers and domain experts. To achieve this, it leverages Zencode which allows them to write and review business logic and data-sensitive operations without learning to code. Like this: 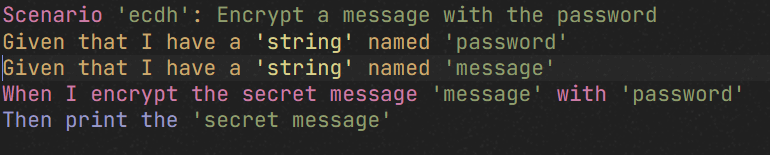 But really what it can do is: - Hashes and signatures (ecdsa, eddsa, Schnorr) - Quantum-proof crypto (Dilithium, Kyber, NTRU) - Homomorphic crypto on BLS381 - Interop with Bitcoin and EVM - Support most widely used curves - Runs on any platform and in the browser - No-code programmabiliy using an English-like DSL We just released [v4.0.0](https://github.com/dyne/zenroom/releases/tag/v4.0.0) and are always interested in more engaging use cases. **Therefor i'd like to extend you an invitation to a webinar this Friday, November 3rd at 4:30pm UTC+1** You can "signup" here: https://zenroom.org/events/ (basically a calendar .ics) If you are uncomfortable with Zoom, please know that the video feed will be relayed to our [Peertube channel](https://diode.zone/c/dynetv/videos) and you will be able to ask questions in the [Matrix chat](https://matrix.to/#/#zenroom:matrix.org). Hoping that i'm not breaking any rules of this community and to see you there i send you all warm regards from planet dyne. edit: removed emoji from title
* https://www.newscientist.com/article/2396510-mathematician-warns-us-spies-may-be-weakening-next-gen-encryption/ * https://news.ycombinator.com/item?id=37866421 * https://news.ycombinator.com/item?id=37756656
 signal.org
signal.org
The article is about: * The Signal Protocol, a set of cryptographic specifications that provides end-to-end encryption for private communications. [PQXDH](https://signal.org/docs/specifications/pqxdh/), an upgrade to the Signal Protocol that adds a layer of protection against the threat of a future quantum computer breaking current encryption standards. * Quantum computing, a new type of computational system that can solve some complex problems faster than classical computers, such as the hidden subgroup problem that underlies many public key cryptosystems4. * Post-quantum cryptography, a new category of algorithms that resist quantum attacks, and how Signal has chosen CRYSTALS-Kyber as its post-quantum key encapsulation mechanism. * The implementation and deployment of PQXDH in Signal’s client applications and the open research areas for further quantum resistance.
 scottarc.blog
scottarc.blog
 piped.video
piped.video
cross-posted from: https://lemm.ee/post/5467810 > In 1997, a contest began to develop a new encryption algorithm to become the Advanced Encryption Standard. After years of debate, one algorithm was chosen as the AES. But how does AES work? And what makes for a secure encryption algorithm? > > *** > > Spanning Tree is an educational video series about computer science and mathematics. See more at https://spanningtree.me > > To be notified when a new video is released, sign up for the Spanning Tree mailing list at https://spanningtree.substack.com/ > > Spanning Tree is created by Brian Yu. https://brianyu.me/ > > Email me at brian@spanningtree.me to suggest a future topic. > > *** > > * 0:00 The Contest > * 1:02 Encryption > * 3:57 Confusion and Diffusion > * 5:44 Block Cipher > * 6:55 KeyExpansion > * 7:34 AddRoundKey > * 8:14 Substitution Cipher > * 8:55 SubBytes > * 11:30 MixColumns > * 12:53 ShiftRows > * 13:21 The Algorithm > > --- > > * https://www.youtube.com/watch?v=C4ATDMIz5wc > * https://piped.video/watch?v=C4ATDMIz5wc > > Aug 22, 2023
 scottarc.blog
scottarc.blog
 www.quantamagazine.org
www.quantamagazine.org
> Yael Tauman Kalai’s breakthroughs secure the digital world, from cloud computing to our quantum future. > My master’s thesis was titled “How to Leak a Secret.” Here’s the problem: We know how to digitally sign — to say, “This is me that wrote this message.” But say I want to sign something as an MIT professor, but I don’t want people to know it’s me? That way the secret does hold some water because you know an MIT professor signed it, but you don’t know who. > We solved this with something we called ring signatures, which were inspired by a notion in computer science called witness-indistinguishable proofs. Let’s say there’s a statement and two different ways to prove it. We say there’s two “witnesses” to the statement being correct — each of the proofs. A witness-indistinguishable proof looks the same no matter which you use: It hides which witness you started with.









